IoT and Regulatory Compliance: Navigating GDPR, HIPAA, and Industry Standards

Key takeaways:
- In IoT, compliance is an architectural property. It’s defined by how data flows across the five layers: device, gateway, cloud, applications, and operations.
- You cannot enforce GDPR or HIPAA without a live data map that tracks data classes, storage locations, access roles, and retention windows across the entire distributed stack.
- GDPR compliance requires data minimization at the edge. This means making engineering decisions on sampling frequency and payload granularity before the hardware is deployed.
- Enterprise auditors now demand evidence of Identity & Access Management (IAM), tamper-resistant audit trails, and a secure OTA (Over-the-Air) update pipeline.
- Mature B2B IoT projects must conclude with an “Evidence Pack”—a set of artifacts including data flow diagrams, KMS configurations, and incident response playbooks—to survive third-party security reviews.
- Compliance priorities shift by domain: healthcare focuses on ePHI isolation; industrial (OT) prioritizes network segmentation (IEC 62443); and energy demands high availability and integrity.
In IoT, compliance is a property of the system, shaped by how data moves, where it’s stored, and who can touch it. No matter, if it’s enterprise IoT solution development, or IoT software development for SMBs, compared to “regular” software, IoT complicates the picture in three ways: the data flow is distributed across devices, gateways, clouds, and integrations; devices stay in the field for years, long after today’s assumptions stop being true; and responsibility is shared across vendors, operators, and internal teams, which makes gaps easy to create and hard to notice.
In this article, we show how to turn GDPR, HIPAA, and common industry standards into engineering decisions. You’ll get a view of controls by layer (device, gateway, cloud, app, operations) and the evidence that auditors and enterprise security teams usually expect to see.
Most importantly, we’ll focus on implementation experience. Knowing the rules matters, but shipping compliant systems in real environments is what reduces risk.
What “compliance” means in IoT projects (and why it’s architecture)
When people say “compliance” in IoT, they often mean encryption, a few policies, and a security review. That helps, but it’s not the core. In practice, compliance is the ability to answer a set of questions under audit pressure about how your system handles regulated data and operational risk.
Start with the data flow, because it dictates almost everything else:
device → gateway → cloud → integrations → analytics/support
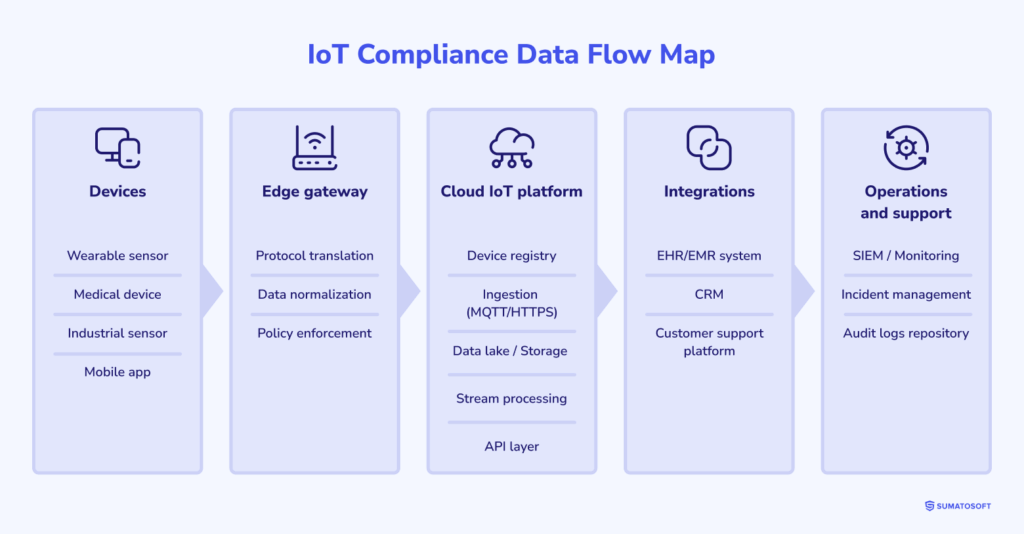
Each hop introduces new failure modes and new owners. Device telemetry may be benign until it can be linked to a person. Gateway buffers can turn into shadow storage. Cloud services multiply access paths. Integrations export data into systems you don’t control. Analytics and support add new audiences, new tooling, and usually new retention needs.
That is why “we encrypt data” is not a compliance statement. Compliance requires:
- Defined roles and responsibilities (who is the controller/processor, or covered entity/business associate)
- Enforceable processes (access management, incident response, change control)
- Evidence (logs, configs, records, test results) that proves the system behaves the way the policy claims it does.
Compliance starts with a data map
Before you debate tools or clouds, fix the data map. At minimum, document:
- Data inventory: what you collect (telemetry, identifiers, health data, logs), and what is considered personal data or ePHI.
- Data flow: where the data travels at each step (device, gateway, cloud services, third-party APIs).
- Storage locations: where data persists (including caches, queues, backups, edge storage).
- Access model: who and what can access it (users, services, devices), and under which roles.
- Retention rules: how long each class of data is kept, and how deletion/expiry is enforced.
- Evidence points: what you can show an auditor (audit logs, IAM policies, encryption/KMS configs, change records, test reports).
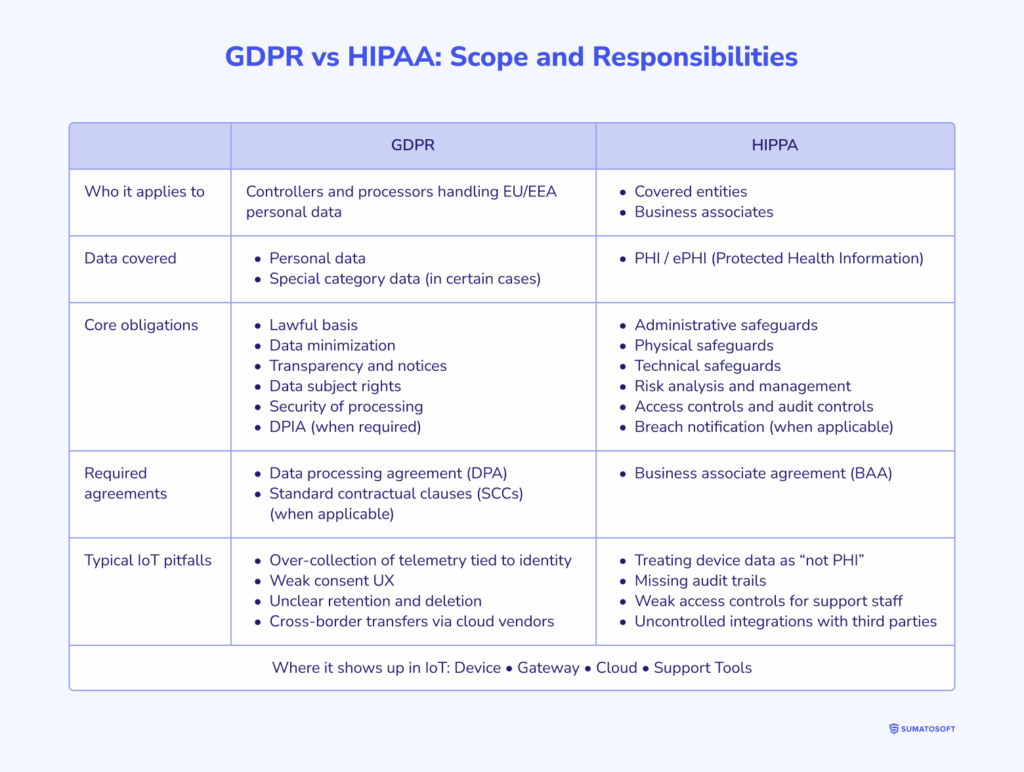
GDPR in IoT: the parts that change system design
Scope: When telemetry becomes personal data
GDPR applies as soon as IoT data relates to an identified or identifiable person. In IoT, that identifiable threshold is often crossed indirectly: a device ID tied to a customer account, location traces, usage patterns, or sensor readings that can be linked back to an individual via other systems. GDPR is explicit that any information relating to an identifiable natural person is personal data.
Lawful basis + purpose limitation: What you must lock down early
You can’t retrofit a lawful basis and purpose limitation after the architecture is set. Before you deploy devices, you want a clean statement of why you collect each data category, who uses it, and what changes are allowed without redesign. That scope drives everything downstream: which services can access the data, what gets exported to third parties, and what you can reasonably keep.
Data minimization: How it affects sampling and payloads
Minimization changes telemetry design: sampling frequency, payload granularity, and whether you stream raw data or derived metrics. GDPR, by design and by default, explicitly frames the amount of data collected, the extent of processing, the period of storage, and accessibility.
Storage limitation + retention: Policy plus technical enforcement
Retention must be enforceable, meaning defined retention windows per data class (telemetry, identifiers, logs), lifecycle rules in storage, deletion workflows that propagate across data stores, and a clear stance on what goes into backups and how long backups are retained.
Rights & requests: Access, deletion, export in a distributed stack
GDPR rights are straightforward on paper and awkward in IoT reality. Access (Art. 15), erasure (Art. 17), and portability (Art. 20) become engineering requirements when data is spread across gateways, streams, databases, analytics stores, and support tooling. You need stable identifiers, traceability (i.e., where data for a given subject exists), and automated workflows that can assemble a response or execute a deletion without disrupting operational monitoring.
Cross-border: What teams usually end up doing
If you use cloud services, CDNs, or contractors outside the EU, cross-border transfer questions arise early in procurement and security reviews. Decision makers typically expect a documented vendor chain, clarity on processing locations, and contract-ready answers on how data moves between regions and third parties (including support access).
When developing IoT solutions, we treat privacy-by-design as a build constraint: we start with a data map, translate it into retention rules that can be enforced technically, and design access paths that are visible in audit logs. This aligns with GDPR’s expectations around data protection by design and appropriate security measures.
HIPAA in IoT: where ePHI shows up and what auditors look for
Where ePHI appears in IoT projects
In healthcare IoT, ePHI appears wherever device or workflow data can be tied to a patient and is created, stored, or transmitted electronically. Typical hotspots include remote patient monitoring (RPM) streams, medical sensor telemetry routed through mobile apps, patient portals that expose measurements and alerts, and imaging workflows where scheduling, referrals, and results are coordinated across systems.
What ePHI means for architecture
HIPAA’s Security Rule is structured around administrative, physical, and technical safeguards. For system design, implications tend to center on a few technical areas: role-based access control, strong authentication, auditable activity logs, encryption in transit and at rest, and disciplined key management. The goal is not merely to “secure data,” but to prove that controls exist and are operating.
Vendors and responsibility: business associates and vendor risk
IoT stacks are vendor-heavy by default: device manufacturers, connectivity providers, cloud services, messaging/notification vendors, and support tooling. In HIPAA terms, that becomes a business associate surface area. Auditors and security teams will press on vendor access, least-privilege boundaries, logging, and whether sensitive data is minimized or de-identified, where full fidelity is not required.
SumatoSoft case study: HIPAA-aligned patient management platform for a dental imaging provider
For a US dental imaging provider, we built a HIPAA-compliant patient management platform that reduces patient wait times and increases branch throughput through predictive scheduling. The solution combined queue orchestration for the walk-in flow with capacity optimization across three branches and integrated with the Client’s scheduler and radiological information system via HL7v2.
On the compliance side, the system was designed to protect ePHI, including encryption, role-based access control, single sign-on, and activity auditing. Historical data used for model training was de-identified, and the ML layer included drift monitoring and scheduled retraining. Operationally, administrators monitored real-time queue status, while critical actions remained under employee control: recommendations were reviewed and confirmed rather than blindly executed.
Industry standards: what we see in RFPs
In RFPs, due diligence calls, and security questionnaires, standards often carry more weight because they translate into expectations about how we isolate networks, how we manage device identities, how we patch systems, and what evidence we can produce.
- IEC 62443 (OT/industrial)
In manufacturing and energy, IEC 62443 pushes companies toward segmentation, controlled conduits between zones, explicit trust boundaries between OT and IT, and a model where availability and safety are first-class requirements. It also forces a sober view of remote access and third-party maintenance, which are common weak points in real deployments.
- NIST baseline for IoT device security
Many teams underestimate how much compliance risk resides at the device layer. NIST guidance is useful because it frames baseline capabilities in device identification, secure configuration, data protection, vulnerability handling, and secure updates. If your device can’t be reliably identified, configured, and updated, the rest of the stack inherits that fragility.
- ISO/IEC 27001 (governance)
ISO 27001 is about how you run security as a system: risk management, policy, access governance, vendor management, incident response, and continuous improvement. In procurement, it’s often the proxy for “this partner can operate in enterprise conditions.” If we see it in the RFP, we expect requests for documented processes and evidence of repeatability.

How SumatoSoft reduces compliance risk as a technology partner
When a buyer says “we need to be compliant,” they’re usually asking for a system that can survive audits and incident reviews. We treat this as an engineering problem, with the goal of building an IoT system in which compliance is a byproduct of controlled access and reliable evidence.
Step 1. We start with a scope that can be implemented
Compliance risk often begins with ambiguity. We reduce that risk by defining the scope in a form that engineering can use:
- What data classes exist (telemetry, identifiers, logs, health-related data)
- Where each class is allowed to flow
- Which systems are allowed to store it
- And which roles are allowed to access it.
This is also where we define what is out of scope because that is often where future exposure hides.
Step 2. We build the data map and keep it alive
A data map is the reference that makes retention, access control, and auditability coherent across a distributed IoT stack. We treat the map as a maintained artifact tied to the architecture:
- Device → gateway → cloud → integrations → analytics/support
- With explicit markers for regulated data touchpoints
- And explicit ownership for each segment (client team, vendor, our team).
That map becomes the index for every compliance conversation that follows: deletion, export, incident response, vendor reviews, and audit evidence.
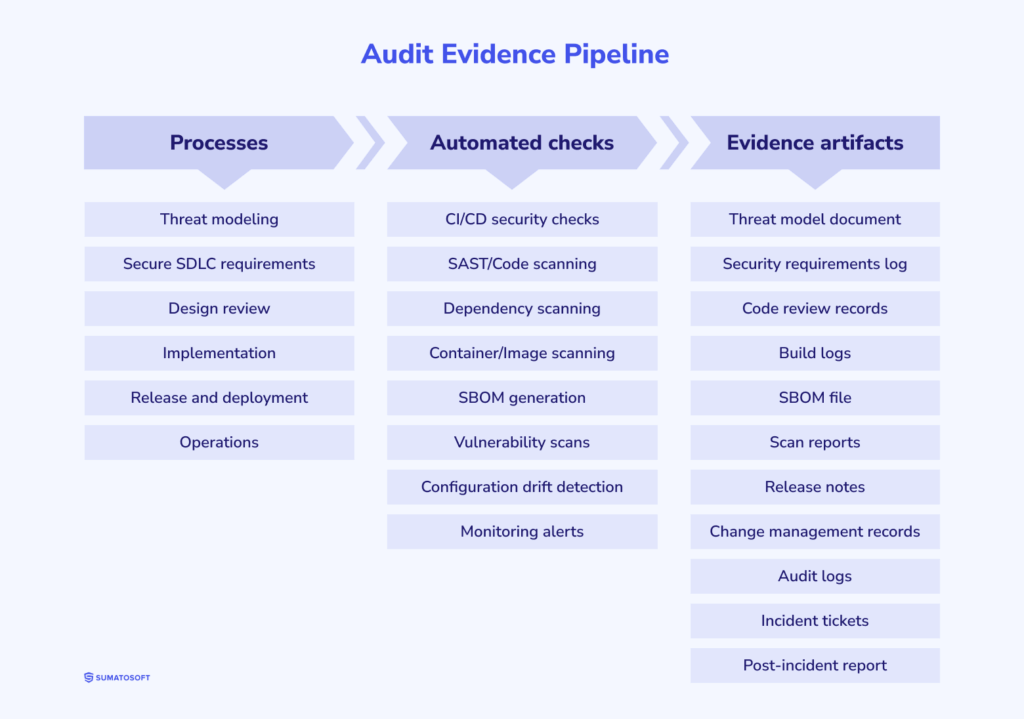
Step 3. We translate requirements into controls per layer
Most compliance failures are cross-layer failures. We address this with a layer-by-layer control model:
- Device: identity, secure configuration, update constraints, minimal local storage
- Gateway: buffering rules, protocol boundaries, northbound authentication, local logging strategy
- Cloud: IAM, encryption, key management, data lifecycle enforcement, segregation of environments
- Apps & portals: session security, role-based access, safe data views, export/deletion workflows
- Operations: monitoring, incident handling, access reviews, and change control.
Step 4. We design for evidence
Evidence is configuration, logs, and repeatable reports that show the claim holds in production.
So we decide in advance:
- Which events must be logged (auth, privileged actions, data access, integration exports)
- Where logs live, how they’re protected, and how long they’re kept
- How you reconstruct an incident timeline without pulling engineers into a week-long excavation.
Step 5. We treat updates and vendor boundaries as compliance surfaces
IoT devices live long enough to outlast your initial risk assumptions.
We plan for:
- Signed firmware and controlled rollouts (including rollback)
- Version visibility across the fleet
- Vulnerability handling with predictable remediation paths
- And integration boundaries that minimize data sharing by default.
In healthcare and industrial environments, we also pay close attention to support access, because remote troubleshooting is where least-privilege often breaks first.
Step 6. We deliver an audit-ready “evidence pack” as part of the project output
We reduce compliance risk when there are left-behind artifacts your team can use. Typical deliverables include:
- Data flow map and data inventory (including regulated data touchpoints)
- Access model (people + services + devices) and role definitions
- Logging and retention design (policy + technical enforcement points)
- IoT update strategy (signing, rollout, rollback, verification)
- Network segmentation and integration boundary diagrams
- And a practical control-to-evidence mapping for audits and security reviews.
Breakdown by domain
The same compliance terms have different meanings in different industries because the data types, risk profiles, and operational constraints vary. Below, we use one consistent template per domain so you can compare what changes, what stays constant, and what that implies for IoT system design.
| Typical data and risks | Main compliance drivers | Architecture implications | Relevant SumatoSoft experience | |
|---|---|---|---|---|
| Healthcare and MedTech IoT | Patient data exposure. | In the US, HIPAA oversees safeguards and auditability. In the EU, GDPR adds privacy-by-design obligations and a need to handle data subject rights. | Equipment telemetry and state data, plus maintenance and operator events. The biggest risks are downtime, unsafe states, and weak remote access. | We built a real-time blood glucose monitoring app that handles sensitive data flows end to end. |
| Manufacturing, industrial, facilities (OT-heavy) IoT | We built a fridge sensor monitoring system with real-time telemetry, alerts, and historical event tracking designed for operational response. | In the US, HIPAA oversees safeguards and auditability. In the EU, the GDPR introduces privacy-by-design obligations and requires the handling of data subject rights. | Design around OT/IT segmentation and explicit trust boundaries. | We built a predictive maintenance platform for HVAC systems with an explicit edge/cloud split, controlled integration points, and audit-ready logging. |
| Energy and renewables IoT | High-frequency telemetry, alarms, event logs, and maintenance signals from distributed assets. Key risks are service disruption, data integrity failures, and insecure remote access. | Availability is usually contract-driven and non-negotiable. Legacy OT/SCADA constraints persist, and buyers expect industrial-grade security controls. | Build alongside existing OT. Logging and incident response must cover the full chain. Updates should be conservative, staged, and reversible. | We delivered an IoT- and ML-based predictive maintenance solution for a wind farm, layering analytics on top of existing infrastructure under real operational constraints. |
| Retail, HoReCa, cold chain IoT | Temperature/humidity, door events, power anomalies, and alert history. Risks are spoilage, missed alarms, and disputes. | GDPR applies when staff/location/account data is involved, but the core need is proving what happened, when. | Make real-time alerting and incident timelines central. Use buffering, consistent event schemas, and retention that supports audits and root-cause analysis. | GDPR and privacy expectations are often the baseline, even outside the EU. App store and platform requirements and contractual obligations shape what gets built. |
| IoT for smart home/smart environments (consumer IoT) | Device states, usage patterns, household identifiers, and app interaction data. Main risks are privacy exposure, account takeover, and unauthorized control. | GDPR and privacy expectations are often the baseline, even outside the EU. App store and platform requirement and contractual obligations shape what gets built. | Treat account security as part of device security. Plan for long-lived devices with a secure update pipeline. | We built IoT apps for controlling an air conditioning system, focusing on secure control paths, reliable connectivity, and disciplined handling of user-linked data at scale. |
Bottomline
SumatoSoft has been building custom software since 2012, delivering 350+ custom solutions for Clients across 25+ countries, with a stated 98% satisfaction rate and 70% senior engineers. In IoT, that experience matters because compliance is solved by how your system is designed: where regulated data appears, how it flows across devices, gateways, cloud services, and integrations, and what evidence you can produce when a customer, auditor, or security team asks for proof.
If you’re planning IoT in a regulated environment, start with a data map workshop. It turns GDPR, HIPAA, and industry standards into a scope covering data classes, access boundaries, retention rules, logging requirements, update strategy, and the audit artifacts you’ll need later.
You can take advantage of our IoT consulting services, IoT security and compliance services, or just contact us to draft the data map and make your IoT network compliant.
Let’s start
If you have any questions, email us info@sumatosoft.com