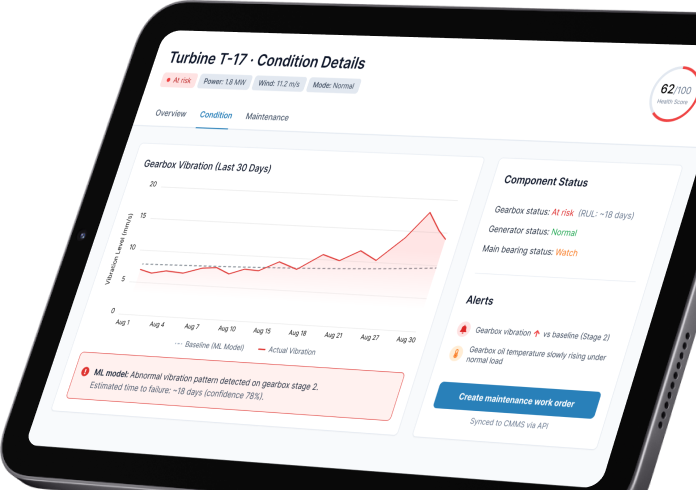
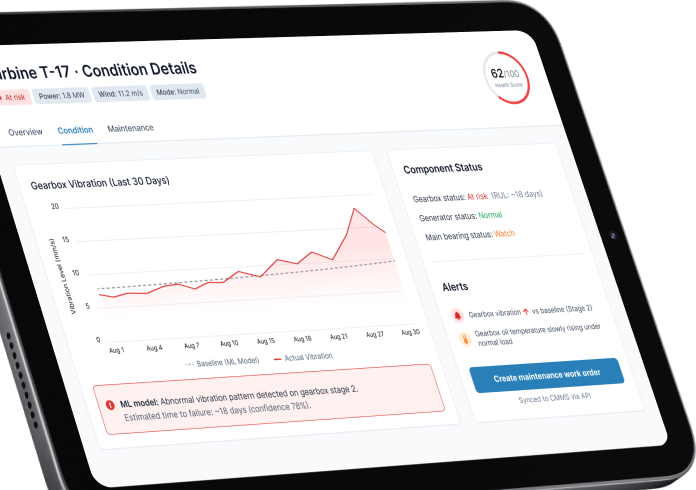
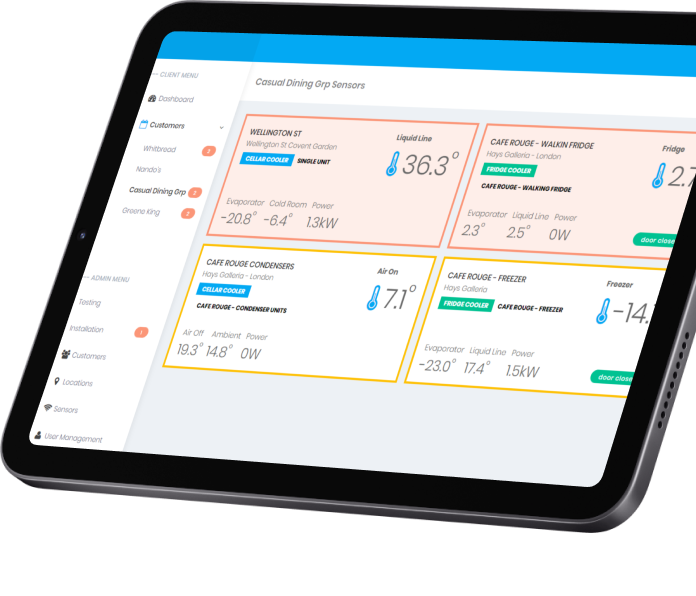
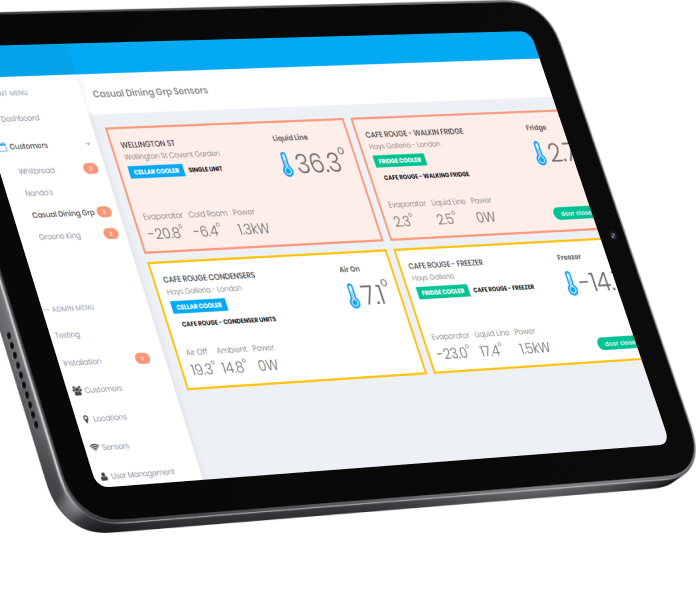
Enterprise IoT solutions development
We develop and integrate IoT platforms for enterprises with distributed assets and complex infrastructure.
What enterprises achieve with enterprise IoT
Enterprise IoT solutions provide businesses with continuous visibility into their assets, equipment, and processes.
With an enterprise IoT system in place, companies:
- See the real state of assets, equipment, and processes in real time.
- Reduce downtime through predictive maintenance and real-time monitoring.
- Replace manual checks with automated data-based alerts.
- Accelerate operational decisions through unified, real-time data.
- Scale operations without losing control or transparency.

Enterprise IoT development services
Enterprises adopt IoT to address specific operational challenges. Our services are structured around these needs, from establishing a stable foundation to scaling the system.
Build a reliable IoT foundation for enterprise scale
We design and develop the core layer that everything else depends on: the software. It includes IoT backend, APIs, and data pipelines. The focus is on stability, predictable performance, and the ability to grow without requiring system redesign later.
Connect devices and sites into one system
We recognize that enterprises typically use a mix of device types and vendors, so we integrate devices, sensors, and gateways from various manufacturers and locations into a unified system. This includes handling multiple communication protocols, unreliable networks, and device-specific data formats, ensuring that all data arrives in a consistent form.
Turn IoT data into operational control
We make the IoT-gathered data work for your business. We implement monitoring, alerts, dashboards, and status views that display what is happening in real-time. Operations teams can identify issues, receive alerts, and understand the system’s state without manually checking devices or logs.
Integrate IoT into enterprise processes
Enterprise IoT development creates value only when the system is integrated with existing business processes. We integrate IoT data with ERP, CRM, BI, and other internal systems, enabling its use in planning, reporting, billing, maintenance workflows, and informed decision-making. This removes manual data transfer and duplicate systems.
Secure the system and manage access at scale
Security becomes increasingly challenging to manage as the number of devices, users, and integrations grows. We implement authentication, role-based access control, encryption, key and certificate management, audit logs, and security monitoring. The system remains governable as users, devices, and integrations expand.
Scale rollout and keep the system running
We support staged rollout, scaling to new locations or devices, performance tuning, and ongoing maintenance. The system can grow and change while remaining available and predictable in production.
Inefficient spare parts and maintenance planning
Uncertainty about when failures will occur forces companies to overstock spare parts or react too late when parts are unavailable. Both scenarios tie up capital and increase operational risk.
Subtle performance degradation goes unnoticed
Small changes in vibration, temperature, load, or efficiency often develop slowly and stay below alarm thresholds. Over time, these inefficiencies increase energy consumption, accelerate wear, and raise operating costs without obvious symptoms.
Unpredictable cost and ownership of PdM systems
SMB are cautious of PdM initiatives that become expensive to scale or require dedicated internal teams. Concerns about platform lock-in, rising subscription costs, and long-term support obligations often slow down or block adoption.
Why enterprises choose SumatoSoft for IoT
Security embedded in delivery
SumatoSoft operates as an ISO-certified company and applies security practices across the entire delivery process. Project confidentiality, controlled access, and compliance with international standards are built into how teams work from the first day.
Vast expertise
We have over 100 specialists on board with over 14 years of experience in the market. We developed over 300 successful apps in 27 countries for 11 business domains.
Full lifecycle responsibility
Our teams cover consulting, architecture, development, integration, testing, cloud, DevOps, and post-launch support. Enterprises work with one accountable partner across the software lifecycle.
Long-term technological partner
We focus on long-term cooperation. Our client’s satisfaction rate with our services is 98%, thanks to our firm commitment to deadlines and their needs. 70% of our clients come back to us with another project.
We work honestly and transparently
We communicate weekly, run demos of the work done, explain potential risks and help to handle them, advise on the decisions, and help to avoid unnecessary costs.
Request a proposal
Receive a detailed project roadmap and budget estimation within 48 hours.
Enterprise IoT solution structure
Enterprise IoT covers multiple layers and dependencies. Our responsibility encompasses the software side, including software development, device connectivity, data processing, and integrations.
IoT platform and backend development
We develop the backend infrastructure that processes data, manages connections, and interacts with users and other applications. The platform is designed to run under high load and scale effectively with the business.
Device, sensor, and gateway integration
We connect heterogeneous devices, sensors, and gateways into a single system. We work with all vendors, protocols, firmware, and data formats.
Data ingestion, processing, and storage
We design pipelines that reliably ingest high volumes of IoT data, validate it, process it in real time, and store it for further analysis and reporting.
Real-time monitoring and alerting
We implement monitoring systems that track device status, health, events, and results in real-time. We set up alerts that trigger automatically when thresholds, failures, or anomalies occur.
Integration with ERP, CRM, BI, and legacy systems
We integrate IoT data with existing modern applications and legacy systems, handling secure data transfer and communication.
Security, access control, and data protection
We implement the latest methods and technologies to secure the data and users. It includes device and user authentication, role-based access control, end-to-end data encryption, network segmentation and isolation, and more.
Our recent works
Industries we build enterprise IoT solutions for
Enterprise IoT is never “one-size-fits-all”. Requirements come from operations: uptime, safety, geography, and regulation. We develop enterprise IoT solutions that align with the industry’s operating reality, tailoring them to real-world conditions and scenarios.
Manufacturing and Industry 4.0
Production leaders measure impact in downtime, throughput, and scrap. If a line stops, the cost impact is immediate. We help unify equipment data across lines and plants, integrating it with existing production systems, so decisions are based on consistent signals.
Healthcare and medical devices
Healthcare requires predictable behavior, auditability, and strong data protection. We develop IoT software with clear access control and traceability, integrating it seamlessly into existing hospital or enterprise IT systems to support compliance and operational continuity.
Energy and utilities
In this domain, failure creates financial and operational risk. Reliability and security are mandatory. We focus on secure data flow, controlled access, and integrations that support centralized monitoring of geographically dispersed infrastructure without expanding the attack surface.
Smart buildings and smart infrastructure
Owners care about measurable outcomes, including cost control, operational visibility, and rapid incident response. We connect building systems into a single management layer and implement monitoring and alerts that operations teams can use across portfolios of facilities.
Logistics and transportation
A logistics network is a dynamic operating environment: assets move, conditions change, and connectivity drops. The system must remain reliable under variable connectivity and field conditions. We build software that maintains operational visibility across fleets, hubs, and regions and integrates with planning and reporting systems.
Retail and commercial facilities
Retail leaders need consistent operations across many locations. A system that works in one site and fails in ten is not scalable. We build centralized monitoring and reporting systems that scale across locations and reduce reliance on ad-hoc, local processes.
Automotive and telematics
Telematics is straightforward in concept but challenging at a production scale, characterized by high data volumes, long device lifecycles, and edge cases in the field. We build platforms that ingest continuous streams, process them in real-time, and remain performant as fleets and functionality expand.
Industrial safety and environmental monitoring
In safety-critical environments, “no data” is an unacceptable state. Monitoring must be reliable, auditable, and traceable. We build systems with resilient data pipelines and event logging that support compliance reporting and incident investigation.
Build Your IoT Team
Scale your capabilities with our pre-vetted senior IoT engineers and architects.
Our development approach
At SumatoSoft, we defined a structured delivery approach that was refined through long-term cooperation with complex systems. This approach allows us to deliver high-quality software on time, within budget, and with fully controlled risks.
Project scoping and alignment
We begin by defining business goals, system boundaries, and success criteria. Our business analyst conducts interviews with stakeholders to clarify requirements, operational constraints, dependencies, project vision, success metrics, and other relevant details. The outcome is a shared understanding of scope and a roadmap with measurable milestones.
Resource planning and team composition
Different projects require different people and skills. We form a delivery team based on the budget, expectation, project complexity, and requirements. Roles and responsibilities are defined upfront across engineering, quality assurance, design, and project management.
Cost estimation and budget control
Our cost estimation is based on detailed task breakdowns, which allows us to commit to the numbers we name at the beginning of the project. Development, testing, design, and analysis efforts are evaluated separately, while our project manager controls the budget execution during the project run.
Risk identification and management
Technical, operational, and delivery risks are identified early. Each risk is assessed for impact and likelihood, with mitigation actions planned and reviewed regularly. We will be caught by surprise, neither will you.
Project scoping and alignment
We begin by defining business goals, system boundaries, and success criteria. Our business analyst conducts interviews with stakeholders to clarify requirements, operational constraints, dependencies, project vision, success metrics, and other relevant details. The outcome is a shared understanding of scope and a roadmap with measurable milestones.
Resource planning and team composition
Different projects require different people and skills. We form a delivery team based on the budget, expectation, project complexity, and requirements. Roles and responsibilities are defined upfront across engineering, quality assurance, design, and project management.
Cost estimation and budget control
Our cost estimation is based on detailed task breakdowns, which allows us to commit to the numbers we name at the beginning of the project. Development, testing, design, and analysis efforts are evaluated separately, while our project manager controls the budget execution during the project run.
Risk identification and management
Technical, operational, and delivery risks are identified early. Each risk is assessed for impact and likelihood, with mitigation actions planned and reviewed regularly. We will be caught by surprise, neither will you.
Knowledge management and documentation
Project knowledge is captured and maintained in our internal system or your system. Documentation covers architecture decisions, system behavior, and operational guidelines. Centralized repositories support onboarding, collaboration, and long-term system maintainability.
Code quality and review practices
We maintain code quality through structured review processes and automated checks. Coding standards, security practices, and architectural guidelines are applied consistently. Reviews are led by senior engineers to ensure maintainability and long-term reliability.
Reporting and delivery transparency
Project progress is tracked and reported on a regular basis. Stakeholders receive updates on completed work, upcoming activities, risks, and dependencies. Demonstrations of delivered functionality support early feedback and alignment.
Post-launch stabilization and warranty
After release, we provide a stabilization period to address issues discovered in production use. This includes bug fixes, performance adjustments, security updates, and preparation for long-term support and evolution.
Security & access control
Aligned with operational risk, not compliance theatre.
Deployment & operations
Designed for long-lived systems.
Knowledge management and documentation
Project knowledge is captured and maintained in our internal system or your system. Documentation covers architecture decisions, system behavior, and operational guidelines. Centralized repositories support onboarding, collaboration, and long-term system maintainability.
Code quality and review practices
We maintain code quality through structured review processes and automated checks. Coding standards, security practices, and architectural guidelines are applied consistently. Reviews are led by senior engineers to ensure maintainability and long-term reliability.
Reporting and delivery transparency
Project progress is tracked and reported on a regular basis. Stakeholders receive updates on completed work, upcoming activities, risks, and dependencies. Demonstrations of delivered functionality support early feedback and alignment.
Post-launch stabilization and warranty
After release, we provide a stabilization period to address issues discovered in production use. This includes bug fixes, performance adjustments, security updates, and preparation for long-term support and evolution.
Security & access control
Aligned with operational risk, not compliance theatre.
Deployment & operations
Designed for long-lived systems.
Enterprise IoT architecture designed to scale
Enterprise IoT solutions must remain stable as device counts, data volumes, and business dependencies grow. We structure enterprise IoT systems into transparent, independent layers, ensuring that growth in one part does not destabilize the rest.
Device and edge layer
Devices, sensors, and gateways collect data and perform basic validation. Edge components are designed to continue operating during connectivity issues and synchronize data once the connection is restored.
Connectivity and data ingestion
We build ingestion pipelines that handle different protocols, unstable networks, and high message throughput. Data is accepted, validated, and queued in a controlled way to prevent loss and overload.
Processing and storage
Data is processed in real-time or in batches, depending on latency and cost requirements. Storage is designed for long-term retention, traceability, and controlled access as data volume grows.
Analytics and intelligence
Rules, analytics, and machine learning are applied where they provide operational value. The system allows analytics to evolve without changes to device firmware or ingestion logic.
Integration
IoT data is integrated with ERP, CRM, BI, and other enterprise systems through stable interfaces. This keeps IoT part of existing business processes instead of a separate operational silo.
Security across the system
Authentication, authorization, encryption, and audit logging are applied consistently across all layers. Access is role-based and managed centrally as the system scales.
Our expertise in tools and technologies
IoT connectivity and data ingestion
- MQTT
- AMQP
- HTTP / HTTPS
- WebSockets
- OPC UA
- Modbus
- AWS IoT Core
Data processing, storage, and operations
- Apache Kafka
- PostgreSQL
- InfluxDB
- TimescaleDB
- Docker
- Kubernetes
- Grafana
Backend development
- Java
- .NET
- Python
- Node.js
- PHP
Frontend and mobile development
- React
- Next.js
- Vue.js
- Django (server-rendered UI / admin interfaces)
- jQuery
- iOS
- Android
- React Native
Talk to an enterprise IoT Expert
Schedule a free 30-minute technical consultation to discuss your challenges.
Enterprise IoT delivery process
Enterprise IoT solutions depend on tight interaction between devices, connectivity, and software. We plan this interaction upfront to ensure hardware evolution and software development stay aligned throughout the project.
We design the target IoT architecture before large-scale implementation begins. Data flows, integrations, security boundaries, and scaling principles are documented and agreed on early. This blueprint guides development and reduces risk during rollout.
We build the solution in controlled iterations. Each iteration delivers a working system component, such as connectivity, data ingestion, processing, integrations, or user interfaces. Progress is visible and measurable.
IoT components are aligned with existing enterprise systems and processes. Data models, workflows, and access control are designed to fit ERP, CRM, BI, and identity management systems already in use.
Enterprise IoT systems are deployed gradually. Rollout may vary by location, device type, or operational unit. This approach keeps production systems stable while the solution expands.
After launch, we support monitoring, maintenance, and controlled evolution of the system. The solution adapts to new requirements and scales without disrupting ongoing operations.
Enterprise IoT challenges we address
We are aware of the challenges enterprises face and address them before they become operational or security risks.
Disconnected systems instead of one operational view
Enterprises often rely on multiple disconnected tools to monitor devices, analyze data, and integrate it into business processes. We consolidate data flows and integrations, enabling IoT to become part of a single operational landscape.
Solutions that stop working after the pilot
The first step in IoT development is designing the system for a small number of devices. However, IoT initiatives might fall into a trap when they work in a pilot, but fail at scale. As the rollout expands, performance deteriorates, costs increase, and stability declines. We design systems that support growth in device count, data volume, and users without re-architecture.
Devices operating with unreliable connectivity
IoT devices often operate with unreliable networks and harsh environments. If the system assumes constant connectivity, unstable networks can lead to data loss and make monitoring unreliable. We build software that tolerates connectivity gaps and synchronizes data safely.
Existing enterprise systems that cannot be replaced
Enterprise environments include legacy platforms that are deeply embedded in the business and cannot be replaced quickly. We integrate IoT solutions with existing systems instead of forcing disruptive changes.
Data that cannot be trusted
If data arrives late, duplicated, incomplete, or inconsistent, teams stop relying on the system. Decisions return to spreadsheets and manual checks. We design ingestion, validation, and processing pipelines that keep data consistent and traceable.
Security that becomes unmanageable at scale
As the number of devices, users, and integrations grows, managing access manually stops working. Without centralized control, security risks increase, and compliance becomes harder to prove. We implement centralized security and access control that scales with the system.
Awards & Recognitions
Let’s start
If you have any questions, email us info@sumatosoft.com