Edge-ready AIoT development that scales with your business
SumatoSoft combines Artificial Intelligence and Internet of Things expertise to build intelligent, connected systems for businesses across all industries. We deploy AI models to devices, keep data flowing, and operate safely at scale.
- pilot scope: devices, data pipeline, dashboards, OTA updates
- targets: <50 ms edge inference, 99.9% fleet uptime, first ROI baseline
- fits: manufacturing, logistics, healthcare, energy
AIoT development services we deliver
Different AIoT development services for different business cases. We connect devices, structure and stream data, add AI where it pays, and deliver dashboards plus OTA to operate safely at scale. Each service plugs into your environment via clear contracts and measurable outcomes.
Embedded firmware for IoT devices
We write and optimize firmware on MCUs/SoCs, wire up sensors/actuators, and tune power profiles. Devices boot reliably, sample accurately, and speak your protocols from day one.
Edge AI design and deployment
We turn AI models into on-device intelligence (TFLite/ONNX/TensorRT), optimize for your hardware, and ship containers/runtimes that act in real time, without constant cloud calls.
Data ingestion and streaming
For this service, we build resilient pipelines from gateways to time-series storage: schema, units, timestamps, deduplication, and replay. Your AIoT apps get clean, current data-no manual fixes.
Cloud backends for IoT
We deliver secure, scalable services for device identity, messaging, storage, and events. Our AIoT solutions are built with IaC and autoscaling, so you can add sites and devices without rework.
AI model development integrated with IoT
As part of our services, we train AI models on your telemetry (anomaly detection, vision, forecasting), wrap them with APIs, and integrate decisions into workflows, alerts, set-points, hold/release.
Real-time monitoring and dashboards
We ship operator views for KPIs, alerts, and guided diagnostics, plus admin consoles for fleet, users, and roles. Issues surface fast, actions are one click away.
OTA updates and remote fleet management
We enable signed and staged OTA for firmware and AI models, as well as health checks and rollback. You can configure, diagnose, and control devices securely from the web or mobile.
Custom AIoT applications
Our core competence is custom AIoT development services. We build the exact mix of edge, web, and mobile you need-dashboards, rules engines, apps for operators and managers-aligned to your process and roles.
System integration and end-to-end testing
This service is about connecting SCADA/MES/ERP/CMMS and verifying contracts, performance, and failure modes. The full stack is tested together, not just in parts.
Security and compliance
We implement per-device identity, encrypted transport, least-privilege access, and SBOMs. Logs and controls align with common standards, so audits go smoothly.
Scalability and infrastructure support
We right-size the edge and cloud, set retention, autoscaling, and cost guards, and keep environments reproducible. As you grow, performance and costs stay predictable.
DevOps, IoTOps, and MLOps
We automate builds, deployments, device provisioning, monitoring, drift checks, and retraining, so your AIoT runs as a holistic, well-thought-out system.
Let’s discuss your AIoT project!
Drop us a line and discuss your project within 1 business day with SumatoSoft AIoT experts.
Industry-focused IoT product development
Healthcare
We connect bedside monitors, wearables, pumps, and lab systems, stream vitals to an event pipeline, and run anomaly AI models for early deterioration signals. Alerts are routed with audit trails and mapped to care pathways. Device data lands in a governed store with PHI segmentation and immutable logs. Clinicians see patient-centric views (trends, risk scores), while operations track bed utilization and device uptime.


Retail
We combine shelf cameras/RFID with POS, loyalty, and supply feeds, run planogram compliance and stockout detection, and trigger replenishment tasks to the right store team. Recommendation and pricing engines use store-level behavior, not just e-commerce data, and tie back to margin targets. Managers see on-shelf availability, shrink heatmaps, and conversion by zone; HQ gets cohort views across stores and seasons.


Manufacturing
We wire machines, PLCs, and vision cameras into one telemetry stream (OPC UA/Modbus, TSDB) and layer anomaly detection, SPC, and defect detection at the edge. Work orders open automatically in CMMS when vibration or temperature crosses thresholds, hold/release ties to MES steps and batch genealogy (ISA-95/88). Dashboards show OEE, FPY, and changeover loss by line and shift, with root-cause drilldowns that trace from alarm, station, lot, and operator.


Smart homes & cities
We connect traffic controllers, CCTV, air-quality and noise sensors, and lighting, apply CV for incident detection, and optimize signal timing and dimming by corridor. Public safety sees flagged events with evidence packages, energy teams view consumption and maintenance queues, and residents get reliable journey times. Rollouts follow district-by-district canaries and respect privacy zones and retention rules.


Transportation & logistics
We stream CAN/J1939, ELD, tire and brake sensors, and cold-chain telemetry, predict component failures, and recompute ETAs from live traffic and handling times. Exceptions create tasks in TMS/WMS and notify customers with accurate windows, yards get camera-based gate counts and dwell analytics. Control towers monitor fleet health, fuel, and SLA adherence across lanes and depots.


Energy & utilities
We ingest AMI/SCADA feeds, weather and tariff data, then optimize set-points for HVAC, pumps, and microgrids with forecast AI models. Edge rules implement demand response and peak shaving without risking comfort or pressure constraints, and leaks are flagged from pressure/flow anomalies with geospatial context. Operators get alarms with playbooks, while finance sees kWh/peak demand and carbon metrics in a shared report.


Agriculture
We deploy soil moisture, EC, weather, and machine telematics, fuse drone/camera imagery for crop stress and disease detection, and drive zone-based irrigation and feeding. Edge logic keeps irrigation schedules running offline, and recommendations adapt by field, cultivar, and phenological stage. Growers view VWC maps, NDVI trends, water use per hectare, and expected yield variance; agronomists export prescriptions to equipment.


Oil & gas
We instrument pipelines and rotating equipment with vibration, corrosion, flow, and pressure sensors, detect leaks and wear early, and correlate alarms with pump curves and maintenance history. Work orders are created with asset IDs, parts lists, and safe-work instructions. Integrity teams see risk scores by segment and environment. Remote sites run safely with store-and-forward and signed OTA to reduce truck rolls.


Construction
We set up site cameras, wearables, and equipment telemetry to detect hazards, track utilization, and validate progress against BIM and the schedule. CV flags PPE violations, proximity risks, and zone breaches with timestamped clips; material deliveries and crane time are reconciled to tasks. Project managers view earned value, idle time, and safety KPIs per subcontractor and area.


Your niche
Get in touch with us and find out how IoT apps can bring value to your business.


Recent software we developed
IoT apps for controlling an air conditioning system

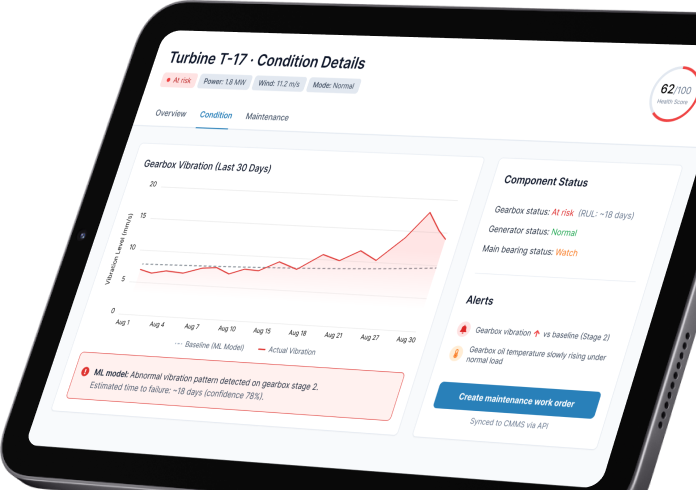
AI-powered predictive maintenance for a large industrial manufacturer


IoT- and ML-based predictive wind farm maintenance
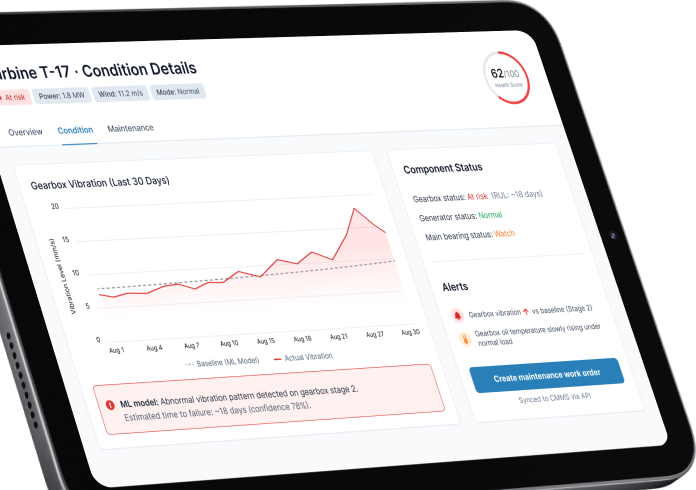
Industrial integrations that matter
Your AIoT only works if it plugs into the plant you already run. When providing AIoT development services, we connect to PLCs and SCADA on the shop floor, sync with MES/ERP/CMMS, and stream to historians and data lakes-using hardened connectors, clear message contracts, and time-synced, unit-normalized telemetry.
MES and shop-floor execution
ISA-95/ISA-88 aligned events (order, batch, step, state). We publish/subscribe via message contracts, so holds, quality gates, and set-point recommendations fit your process, not the other way around.
ERP and inventory
SAP, Oracle, Microsoft Dynamics. We sync materials, lots, work orders, and cost centers to make ROI visible in the system’s finance trusts.
CMMS and maintenance
IBM Maximo, SAP PM, Fiix. AI alerts create work orders with the right asset IDs and parts, completions feed back to retrain AI models and refine thresholds.
Historians and data lakes
OSIsoft/AVEVA PI, Ignition, Kafka, time-series DBs, cloud warehouses. We de-duplicate, version, and tag lineage so analytics don’t break when tags or assets change.
Building, energy, and utilities
BACnet, Modbus, AMI/SCADA energy data. We surface leak/overuse alerts and push set-point changes with audit trails to cut kWh without risking comfort or safety.
Fleet, logistics, and telematics
CAN/J1939, ELD, TMS/WMS/OMS. We correlate vehicle health, routes, and loads for fewer breakdowns and tighter ETAs.
Healthcare and regulated flows
HL7/FHIR, DICOM, GxP data controls. We keep PHI segregated, signed, and auditable while still enabling real-time monitoring and alerts.
Computer vision on the line
Cameras, PLC interlocks, and CV services integrate via low-latency topics, hold/release and reject bins are triggered deterministically.
Roadblocks we remove before we start
There are roadblocks that might hinder the development if not removed in time. Before writing a single line of code, we ensure the development process will go smoothly and without any undesired surprises. This is the starting point of our services where we prepare a plateau for success.
We turn data chaos into a clean, queryable stream
Problem: fragmented schemas, noisy sensors, missing timestamps.
Fix: device-level validation, time sync, unit normalization, and a canonical telemetry schema.
Deliverables: data contracts, mapping doc, sample TSDB with 7-day replay.
We unify heterogeneous devices into one manageable fleet
Problem: mixed PLCs, gateways, OS versions, and protocols.
Fix: device matrix, protocol adapters (MQTT/OPC UA/Modbus), and a unified provisioning flow.
Deliverables: fleet registry, provisioning runbooks, golden images.
We quantify ROI before we build the pilot
Problem: vague goals, moving targets, no baseline.
Fix: KPI tree and ROI model tied to a single line/site.
Deliverables: pilot charter with success criteria (e.g., -15% downtime, -8% scrap, +10% OEE).
We enforce a secure-by-default posture
Problem: open ports, shared creds, unsigned firmware/models.
Fix: Zero-trust comms, per-device identities, signed OTA, least-privilege access.
Deliverables: security baseline, SBOM, key/secret rotation plan.
We integrate legacy systems with proven connectors
Problem: brittle links to SCADA/MES/ERP/CMMS.
Fix: hardened connectors and message contracts with back-pressure and retries.
Deliverables: interface specs, staging sandbox, failure-mode tests.
Data chaos
Problem: fragmented schemas, noisy sensors, missing timestamps.
Fix: device-level validation, time sync, unit normalization, and a canonical telemetry schema.
Deliverables: data contracts, mapping doc, sample TSDB with 7-day replay.
Heterogeneous devices
Problem: mixed PLCs, gateways, OS versions, and protocols.
Fix: device matrix, protocol adapters (MQTT/OPC UA/Modbus), and a unified provisioning flow.
Deliverables: fleet registry, provisioning runbooks, golden images.
ROI calculation
Problem: vague goals, moving targets, no baseline.
Fix: KPI tree and ROI model tied to a single line/site.
Deliverables: pilot charter with success criteria (e.g., -15% downtime, -8% scrap, +10% OEE).
Security
Problem: open ports, shared creds, unsigned firmware/models.
Fix: Zero-trust comms, per-device identities, signed OTA, least-privilege access.
Deliverables: security baseline, SBOM, key/secret rotation plan.
Legacy systems
Problem: brittle links to SCADA/MES/ERP/CMMS.
Fix: hardened connectors and message contracts with back-pressure and retries.
Deliverables: interface specs, staging sandbox, failure-mode tests.
We make AI models deployable on target edge devices
Problem: small/noisy datasets, cloud-only AI models that won’t run on device.
Fix: data sampling plan, feature store, and edge optimizations (quantization/pruning).
Deliverables: baseline model card, on-target latency/accuracy report.
We design pipelines that tolerate bad connectivity
Problem: flaky networks, rural sites, cellular caps.
Fix: store-and-forward buffers, offline rules, differential sync.
Deliverables: connectivity playbook, SLA/SLOs for ingest and alerting.
We make TCO transparent and predictable
Problem: hidden cloud egress, oversized hardware, tool sprawl.
Fix: capacity estimates, right-sized edge, and cost guards.
Deliverables: TCO sheet (edge/cloud), autoscaling & retention policies.
We align stakeholders around one decision path
Problem: ops vs. IT vs. data science priorities.
Fix: RACI, weekly pilot cadence, change window policy.
Deliverables: governance charter, escalation matrix, risk register.
We ship safe, staged OTA updates at scale
Problem: fear of bricking devices and model drift.
Fix: staged rollouts, health checks, instant rollback.
Deliverables: OTA runbook, canary plan, rollback tests passed.
AI models
Problem: small/noisy datasets, cloud-only AI models that won’t run on device.
Fix: data sampling plan, feature store, and edge optimizations (quantization/pruning).
Deliverables: baseline model card, on-target latency/accuracy report.
Bad connectivity
Problem: flaky networks, rural sites, cellular caps.
Fix: store-and-forward buffers, offline rules, differential sync.
Deliverables: connectivity playbook, SLA/SLOs for ingest and alerting.
TCO transparency
Problem: hidden cloud egress, oversized hardware, tool sprawl.
Fix: capacity estimates, right-sized edge, and cost guards.
Deliverables: TCO sheet (edge/cloud), autoscaling & retention policies.
Stakeholders alignment
Problem: ops vs. IT vs. data science priorities.
Fix: RACI, weekly pilot cadence, change window policy.
Deliverables: governance charter, escalation matrix, risk register.
OTA updates
Problem: fear of bricking devices and model drift.
Fix: staged rollouts, health checks, instant rollback.
Deliverables: OTA runbook, canary plan, rollback tests passed.
Blueprints for every AIoT system: edge, cloud, hybrid
There are 3 architecture types for AIoT systems. Our Tech Lead with 10 years of experience in designing IoT systems and over 4 years of designing AIoT systems draws an optimal architecture for your business case. Moreover, they show you how data moves, where intelligence lives, and how updates flow, so you know how your systems operate and stay from day one.
Edge – decisions close to the device
- When to use: real-time control, limited connectivity, data-sensitive sites.
- Typical stack: sensors/PLCs, gateway (containers, rules engine), local store (TSDB), periodic cloud sync.
- Data flow: Device, Gateway (preprocess + model), Actuator, batched summaries to cloud for history.
- OTA path: cloud OTA service, staged rollout, gateway/device, health check, promote/rollback.
Cloud – central analytics and fleet orchestration
- When to use: heavy analytics, cross-site insights, simpler edge devices.
- Typical stack: devices, secure messaging (MQTT/HTTPS), ingestion, data lake/warehouse, model training/serving, dashboards/APIs.
- Data flow: Device, Cloud ingest, Processing/ML, Apps, actions returned via commands.
- OTA path: cloud OTA, device groups, verify, roll back if needed.
- Trade-offs: maximum scalability and governance, depends on reliable connectivity.
Hybrid – real-time at the edge, deep learning in the cloud
- When to use: most industrial and multi-site scenarios.
- Typical stack: edge inference + rules, cloud for retraining, fleet management, long-term storage.
- Data flow: Device, Edge model (immediate action), Cloud (history, retrain), New model, Edge.
- OTA path: model/firmware signed in cloud, canary at edge, fleet rollout with health gates.
- Trade-offs: balanced latency and insight depth, requires clear contracts between edge and cloud.
Quick playbook: planning AIoT development project [pdf]
Get a free playbook that will help you plan the project and find the right AIoT development partner. No email required.
What you get in the first 12 weeks
We ship new deliverables weekly or biweekly when providing AIoT development services. Each deliverable has an owner, acceptance criteria, and a demo, so you can see progress as we move along the plan.
- Pilot charter: line/site, KPIs, success thresholds, ROI model.
- Device & data audit: device matrix, protocol map, data contracts, 7-day replay TSDB.
- Security baseline: identities, access model, SBOM, key rotation plan
- Architecture draft: edge/cloud/hybrid reference, OTA path, integration points (SCADA/MES/ERP/CMMS).
- Go/No-Go kit with risks, mitigations, and timeline.
- Connectivity in place: adapters for MQTT/OPC UA/Modbus, store-and-forward buffers
- Clean stream: time sync, unit normalization, schema enforcement in a canonical telemetry model
- Data platform: time-series DB + warehouse landing, feature store stubbed for ML
- Runbooks: provisioning, fleet registry, connectivity playbook with SLOs
- Edge runtime: gateway containers, rules engine, signed OTA pipeline (canary + rollback).
- First ML baseline: An anomaly or vision model is trained on your data, and a model card is issued.
- On-target test: latency/accuracy/power are measured on the chosen device, and optimization (quantization/pruning) is applied.
- Safety nets: offline mode, back-pressure, and retries validated.
- Operator dashboard: live KPIs, alerts, guided diagnostics, audit trail.
- Closed loop: alert, action rules (hold/release, set-point recommendations).
- Integration harness: messages/contracts to SCADA/MES/ERP/CMMS in staging.
- Security hardening: zero-trust comms, secrets management, and least-privilege roles enforced.
- Limited rollout on one line/area with the canary cohort.
- Monitoring: ingest SLOs, inference latency, model drift, device health
- Data quality gates: completeness >99%, late/duplicate handling, lineage tracking
- Incident playbook: alert routing, on-call, change windows, rollback test passed
- Impact report: before/after deltas on downtime, yield, energy, cycle time, attribution by intervention
- TCO & payback: updated cost model, scale scenarios with right-sized edge and cloud
- Handover: admin training, runbooks, dashboards, IaC/recipes, access provisioning
- Next step: scale roadmap (sites/devices), compliance checklist, MLOps/IoTOps SLAs
Outcomes you can expect
We don’t guess, we measure. Each outcome of our services ties to a measurable metric, which, in turn, ties to a named data source (PLC/SCADA, CMMS, QMS, TSDB). We agree thresholds up front, show before/after on a shared dashboard, and attribute gains to specific interventions to avoid “analytics inflation”.
Fewer stoppages, higher uptime
Better quality, less scrap
Predictive maintenance that pays back
Energy and consumables under control
Real-time decisions at the edge
Safer operations, cleaner compliance
Faster throughput, shorter lead times
Clear ROI, not just dashboards
Pricing model for AIoT development projects
We offer the pricing models for AIoT development services that is known for its flexibility. It fits the best for the development of high-tech projects requiring R&D effots.
The Time & Material engagement model implies monthly billings that contain only real development efforts in the previous month (person-hours actually worked). It’s most suitable for:
AIoT tech expertise from chips to cloud
From device firmware to cloud analytics and everything in between, we build AIoT systems that actually run in the field. Our AIoT expertise covers the most modern and in-demand technologies.
Connectivity & field protocols
- MQTT, OPC UA, Modbus/TCP, CAN, BLE, Wi-Fi, LTE/5G, LoRaWAN;
- gateway containers, rules engines, store-and-forward buffers;
- per-device identity, cert provisioning, encrypted transport.
Data pipelines & storage
- time-series ingest with schema/units normalization;
- TSDB + data lake/warehouse, feature stores for ML;
- data contracts, lineage, retention, and replay for testing.
Machine learning & edge inference
- anomaly detection, forecasting, CV (defect detection, tracking);
- model cards, on-target latency/accuracy/power validation;
- retraining pipelines, A/B and canary deployment for AI models.
Applications & UX
- operator dashboards (KPIs, alerts, guided diagnostics);
- admin consoles (fleet, users, roles, audit trails);
- role-based access, internationalization, offline modes.
Ops: IoTOps + MLOps
- fleet registry, health telemetry, OTA firmware/model updates;
- monitoring for ingest, inference, drift, incident runbooks;
- IaC for repeatable environments, change windows and rollbacks.
Industrial integration
- SCADA/MES/ERP/CMMS connectors with back-pressure and retries;
- message contracts (commands, events) and staging sandboxes;
- batch and event-driven flows to existing systems.
IoT development
- AWS IoT Core
- AWS IoT Device Defender
- AWS IoT Device Management
- AWS IoT Events
- Azure Data Lake
- Azure Digital Twins
- Azure IoT Central
- Azure IoT Hub
- Azure Kinect
- Google Cloud Datastore
- MLlib
- ThingSpeak
AI development
- Amazon S3
- Azure Blob Storage
- Databricks
- PyTorch
- TensorFlow
- XGBoost
- LightGBM
- ResNet
- YOLO
- GPT-4
- Claude
- Llama
- DALL-E
- Stable Diffusion
- AWS SageMaker
Security by design for AIoT
Security isn’t a bolt-on – it’s built into every layer of our AIoT systems. We build systems that are secure across gateways, devices, firmware, OTA updates, and data flows. When providing AIoT development services, we leverage multiple methods and techniques to secure the system.
Per-device identity and zero-trust comms
Every device gets its own certificate, all links use mutual TLS, networks are segmented and deny-by-default.
Threats this measure handles: credential sharing, device impersonation, lateral movement, and man-in-the-middle.
Secure and measured boot
Firmware integrity is verified at startup (TPM/TEE, where available), storage is encrypted, and debug ports are locked.
Threats this measure handles: bootloader tampering, firmware backdoors, and data theft from stolen devices.
Signed, staged OTA
Firmware and model updates are signed, canaried, health-checked, and rolled back on failure.
Threats this measure handles: malicious updates, supply-chain injection, fleet-wide bricking.
Data minimization at the edge
Sensitive fields are filtered/anonymized/aggregated before leaving the site, and data is encrypted in transit and at rest.
Threats this measure handles: privacy leaks, excessive data exposure, interception during transport.
Least-privilege access
Fine-grained roles for users, services, and devices, keys and secrets are vaulted and rotated.
Threats this measure handles: privilege escalation, stale/compromised credentials, insider misuse.
Compliance-ready controls
Data classification, retention, and access logging aligned with ISO 27001/SOC 2/GDPR expectations.
Threats this measure handles: regulatory non-compliance, over-retention of PII, unauthorized access.
Per-device identity and zero-trust comms
Every device gets its own certificate, all links use mutual TLS, networks are segmented and deny-by-default.
Threats this measure handles: credential sharing, device impersonation, lateral movement, and man-in-the-middle.
Secure and measured boot
Firmware integrity is verified at startup (TPM/TEE, where available), storage is encrypted, and debug ports are locked.
Threats this measure handles: bootloader tampering, firmware backdoors, and data theft from stolen devices.
Signed, staged OTA
Firmware and model updates are signed, canaried, health-checked, and rolled back on failure.
Threats this measure handles: malicious updates, supply-chain injection, fleet-wide bricking.
Data minimization at the edge
Sensitive fields are filtered/anonymized/aggregated before leaving the site, and data is encrypted in transit and at rest.
Threats this measure handles: privacy leaks, excessive data exposure, interception during transport.
Least-privilege access
Fine-grained roles for users, services, and devices, keys and secrets are vaulted and rotated.
Threats this measure handles: privilege escalation, stale/compromised credentials, insider misuse.
Compliance-ready controls
Data classification, retention, and access logging aligned with ISO 27001/SOC 2/GDPR expectations.
Threats this measure handles: regulatory non-compliance, over-retention of PII, unauthorized access.
We keep your AIoT smart: MLOps and IoTOps built-in
MLOps and IoTOps are how your AIoT system keeps working after launch. MLOps manages the brains: it gets AI models from the lab into production, watches their accuracy in the real world, and updates them safely when data or conditions change. IoTOps manages the machines: it onboards devices in bulk, tracks their health, pushes safe over-the-air updates, and keeps data flowing even with spotty networks. Together, they cut downtime, prevent silent errors, and let you scale from one site to many without surprises.
MLOps – AI model operations
- version everything: datasets, features, AI models, and inference images have IDs and lineage;
- one-click deploy to edge or cloud serving, canary and A/B supported;
- live monitoring of accuracy, drift, latency, and resource use tied to each model version;
- automated retraining pipelines on new data or drift triggers, human approval before promotion;
- model cards with on-device validation (latency, power, accuracy) and rollback snapshots;
- comprehensive governance that includes access controls, audit trails, reproducible builds, and signed artifacts.
IoTOps – device & fleet operations
- fleet registry with per-device identity, health, config, and ownership;
- provisioning at scale: golden images, bootstrap scripts, and secure enrollment;
- signed OTA for firmware and AI models with staged rollouts and health gates;
- telemetry you can act on: ingest SLOs, device vitals, link quality, error budgets;
- resilience patterns: store-and-forward, back-pressure, offline rules, safe modes;
- incident playbooks: alert routing, change windows, rollback steps, post-incident notes.
Why SumatoSoft is the right AIoT development company
Since 2012, we’ve helped companies turn new IT ideas into a competitive advantage-IoT and now AIoT included. Over the years, we’ve built, integrated, and scaled connected systems end to end: from device firmware and secure connectivity to data pipelines, ML models, and the apps and ops that run them. Along the way, we distilled clear, non-negotiable practices for reliable AIoT delivery that we apply when providing our services. Today, we’re a trusted software partner for businesses in 26 countries, including the US.
End-to-end expertise
Security mastery
Operable by design (MLOps + IoTOps)
Transparency & ongoing support
Industrial integrations that don’t break production
Edge performance proven on your devices
For 13+ years, we have proudly taken responsibility for your AIoT projects!
Awards & Recognitions
Let’s start
If you have any questions, email us info@sumatosoft.com

Frequently asked questions
What is the AIoT system?
An AIoT system is the integration of Artificial Intelligence (AI) with the Internet of Things (IoT), creating intelligent, interconnected devices that can analyze data and make autonomous decisions in real-time.
What is AIoT in healthcare?
AIoT in healthcare is the integration of artificial intelligence with the Internet of Things to create a network of smart medical devices and sensors that can analyze health data in real-time to improve patient outcomes and operational efficiency.
What is the difference between IoT and AIoT?
While IoT connects devices to the internet to gather data, AIoT adds artificial intelligence to that data, enabling those devices to learn, analyze, and make intelligent decisions without human intervention.
How much does AIoT development cost?
The cost of AIoT development can range from a few thousand dollars for a simple prototype to several million for a complex, enterprise-grade system, as it is highly dependent on factors like hardware complexity, software features, AI model sophistication, and the expertise of the development team.
What are the key components of an AIoT system?
The key components of an AIoT system are interconnected smart devices with sensors, a communication network, and a central or edge-based platform that uses artificial intelligence to analyze data and generate insights.



















