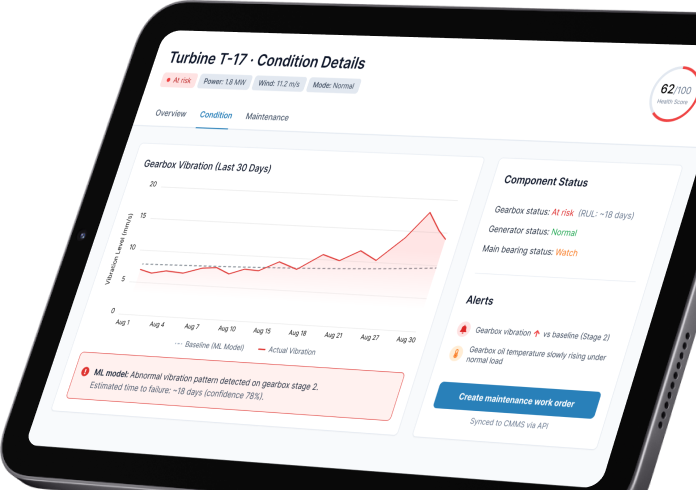
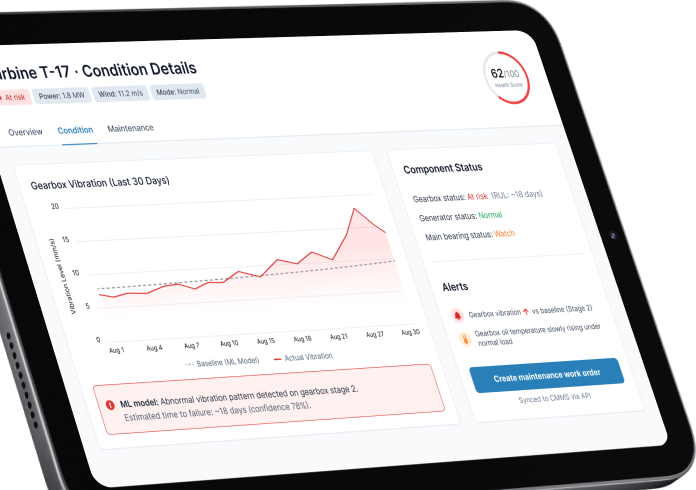
IoT security and compliance services
SumatoSoft audits existing IoT networks for security and compliance, provides consulting services to businesses concerned with the security of their IoT systems, and designs IoT systems from scratch that meet regulatory requirements. We provide IoT security at the device, network, cloud, and application levels.
Key areas where we strengthen your IoT system
Our IoT security and compliance services
Below are the main areas in which SumatoSoft works with IoT security. We flexibly assemble the proper service set for your product and industry.
Risk assessment and threat modeling
- We start by understanding exactly what needs to be protected. To do that, we conduct an IoT risk assessment and compile an asset map.
- Next, we perform IoT threat modeling for key scenarios, drawing on best practices and real-world attack cases.
- As a result, you receive a prioritized list of risks with a change plan for devices, networks, the cloud, and processes.
Secure architecture and development
- We design IoT architecture with IoT cybersecurity and compliance in mind. We define network zones, encryption methods, and authentication points.
- The team implements these solutions into the code and infrastructure, laying the foundation for secure IoT solutions.
- We use a secure development, testing, and release cycle, and security doesn’t slow down feature delivery; it’s built into the proce
Compliance and regulatory requirements
- We cover regulatory compliance for IoT tailored to your market.
- We work with IEC 62443 compliance for IoT in industrial environments.
- We develop solutions that pass inspections more easily in factories and on the shop floor.
- For IoT in the EU, we build GDPR compliance for IoT devices.
- We configure consent collection, storage, anonymization, and data deletion rights.
- We rely on the NIST IoT cybersecurity framework guidelines where relevant.
- We document policies and artifacts that auditors and security teams expect.
Firmware and secure OTA updates
- Firmware is a common entry point for attacks.
- We strengthen IoT firmware security and build processes for secure OTA updates.
- We add signatures, integrity checks, and secure rollback capabilities, while accounting for device memory, network, and power limitations.
- The result is a managed update process critical to IoT vulnerability management and the closure of discovered vulnerabilities.
Device identity and authentication
- We configure IoT device identity management (IoT) so each device has a stable digital identity.
- We implement IoT device identity management solutions and use certificates, secure key storage, and rotation.
- We build IoT device authentication and identity management, so only trusted devices can connect to your network and services.
- This reduces the risk of device spoofing and man-in-the-middle attacks.
Data protection and encryption
- We take responsibility for IoT data encryption throughout the operational lifecycle: data is encrypted on the device, in transit, and in storage.
- We restrict data access by role and scenario and log access, changes, exports, and attempts to bypass rules.
- This is important for personal data, trade secrets, and telemetry, and builds trust in the platform and ensures compliance.
Security testing and vulnerability management
- We conduct IoT penetration testing across device, application, and cloud layers. This includes IoT penetration testing services according to the agreed-upon scope.
- We use IoT vulnerability assessment tools and services to identify weaknesses before attackers find them.
- We then integrate IoT vulnerability management as a process by recording vulnerabilities, setting deadlines, and repeating checks.
Industry service packages
- For healthcare, we consider HIPAA, GDPR, medical device requirements, and patient risks.
- For manufacturing and OT, we focus on network segmentation, IEC 62443, and line and equipment access.
- For industrial IoT platforms, we connect standard requirements with controls in your stack.
- This way, you receive an IoT security action plan tailored to your business, industry, and regulators.
Why SumatoSoft is your IoT security and compliance partner
Certifications
Audits
Regulations
Standards
Let’s discuss your IoT security case!
Drop us a line and discuss your project within 1 business day with SumatoSoft IoT experts.
IoT vulnerabilities that we address
| Vulnerability type | Issues | Our solutions |
|---|---|---|
Typical device issues |
|
|
Network and cloud-level vulnerabilities |
|
|
Compliance and industry requirements |
|
|
Vulnerability type
Typical device issues
Network and cloud-level vulnerabilities
Compliance and industry requirements
Issues
- Firmware is challenging to update, firmware-over-the-air is poorly designed, and there is no version control.
- No bootloader protection; firmware can be easily changed or read with physical access.
- Device identity is not managed: shared logins and copying keys from an image.
- Devices are connected to the general network without segmentation or filtering.
- Traffic is not encrypted, and legacy protocols are used.
- Cloud services are configured by default to grant unnecessary privileges to administrators and service accounts.
- Medical data (GDPR compliance for IoT devices and HIPAA) requires clear access and logging rules.
- Industry is awaiting IEC 62443 compliance for IoT and a well-thought-out risk profile.
Our solutions
- Strengthening IoT firmware security and the update process.
- Building secure OTA updates for IoT devices with signatures, integrity checks, and rollbacks.
- Introducing IoT device identity management solutions with certificates and rotation.
- IoT data encryption and proper cloud configuration.
- Encryption in the channel and in storage, access restriction, and closing unnecessary entry points.
- IoT penetration testing and IoT vulnerability assessment to identify vulnerabilities.
- Connecting IoT cybersecurity, IoT vulnerability management, and legal requirements to make your platform trustworthy to auditors, partners, and internal stakeholders.
Industries’ IoT security requirements we cover
Healthcare and MedTech
- Regulations: HIPAA, FDA guidance, IEC 80001.
- Controls: data encryption, strict roles, channel security, device management.
- Quick wins: access logging, OTA control, API settings verification.


Manufacturing & OT
- Regulations: IEC 62443, NIST SP 800-82.
- Controls: segmentation, secure OPC UA, rights management on factory floor networks.
- Quick wins: line isolation, traffic filtering, firmware auditin.


Smart Buildings & PropTech
- Regulations: GDPR, ETSI EN 303 645.
- Controls: personal data management, privacy settings, channel security.
- Quick wins: device encryption, API control, firmware updates.


Logistics & Transport
- Regulations: data security requirements and cargo safety obligations.
- Controls: tracker and gateway protection, telemetry integrity verification.
- Quick wins: network rule verification, cloud access control, message signing.


Consumer IoT
- Regulations: ETSI EN 303 645.
- Controls: Unique credentials, traffic protection, secure updates.
- Quick wins: eliminating default passwords, OTA verification, request filtering.


Fintech
- Regulations: PCI DSS.
- Controls: Payment data protection, strict roles, API control.
- Quick wins: Payment function isolation, separate keys for transactions.


IoT security regulations readiness
IoT security regulations evolve worldwide, and at SumatoSoft, we stay on top of these changes to ensure our Clients’ businesses remain compliant and secure. These are not all, but the most requested regulations we follow:
EU Cyber Resilience Act (CRA)
Expected to be enforced by 2027, this act introduces mandatory security-by-design principles and lifecycle support for products with digital elements.
UK Product Security & Telecommunications Infrastructure (PSTI) Act
A UK law that bans default passwords in consumer IoT devices and requires transparency about security update support and vulnerability disclosure policies.
EU NIS2 Directive
An expanded EU cybersecurity directive that extends requirements to more sectors (including critical infrastructure using IoT) and imposes stricter risk management, incident reporting, and supply chain security obligations.
NIST IoT Cybersecurity Framework
A U.S. framework from NIST that outlines best practices for secure IoT development and risk management.
FDA Medical Device Cybersecurity Requirements
U.S. FDA guidance has ramped up cybersecurity expectations for IoT medical devices, requiring manufacturers to address security in pre-market submissions and to maintain post-market monitoring and updates.
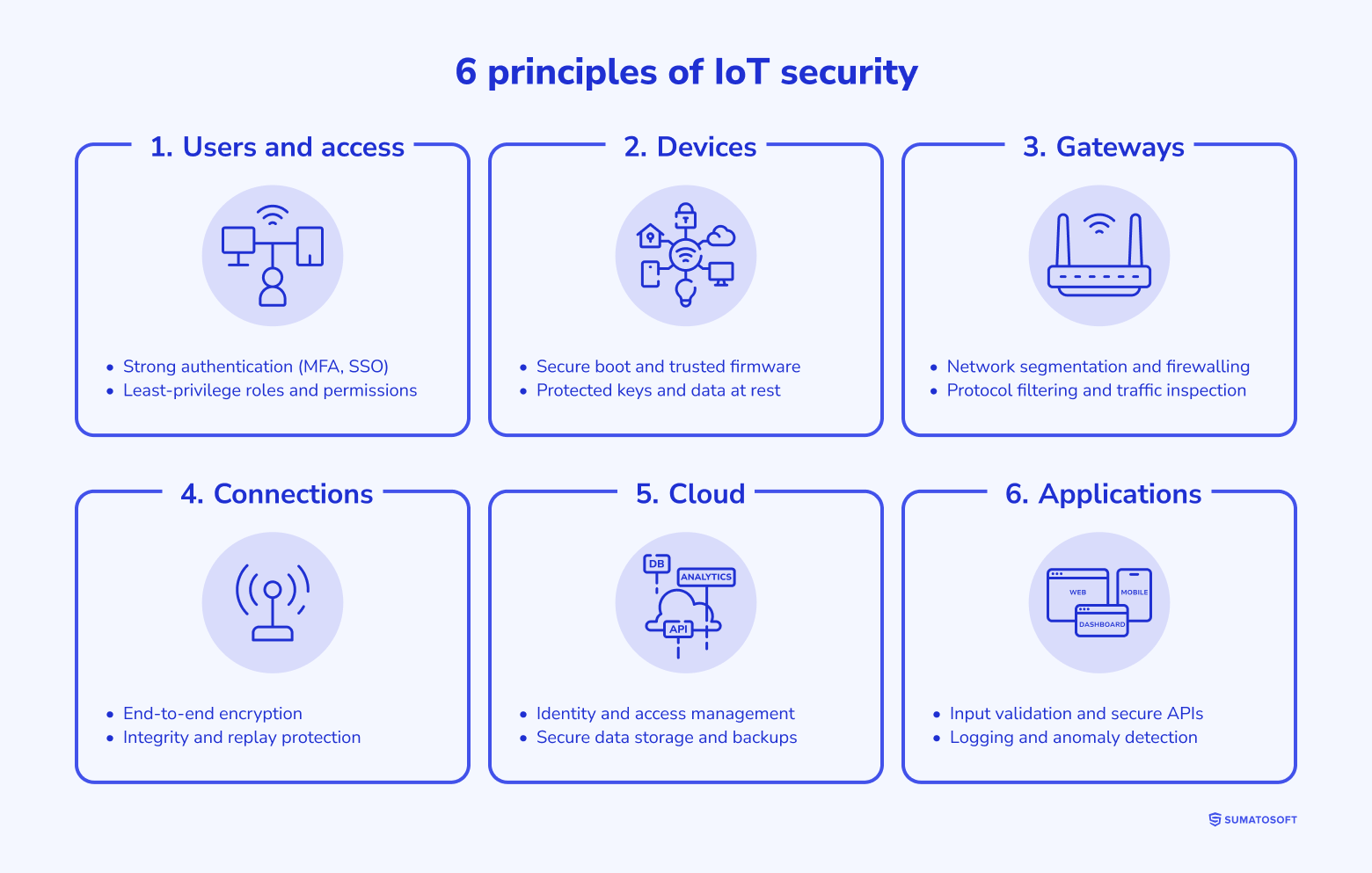
6 principles of IoT security
Our mandatory six principles help build IoT security at the device, network, cloud, and application levels and simplify subsequent compliance.

Quick playbook: selecting an IoT development partner [pdf]
Get a free playbook that will help you find the right IoT development partner. No email required.
Recent IoT software we developed
IoT technologies we work with
Our IoT security and compliance process
We begin by examining your current IoT system. Unlike developing from scratch, security requires analyzing the existing architecture, data, firmware, and operations. The goal is to understand the risks, mitigate vulnerabilities, and ensure the solution complies with the required standards.
We conduct an audit of the existing IoT platform: examine devices, the network, the cloud, APIs, and support processes. Then, we analyze threats, identify technical gaps, and regulatory incompatibilities. This helps us understand what needs to be changed and in what order.
We analyze your architecture and data landscape: how devices operate, how messages flow, and how keys are stored. We then compare the approaches against IEC 62443, GDPR, HIPAA, and other applicable regulations. The result is our proposal of changes that strengthen the system without complex redesigns. For clarity, we create a document with checkpoints and recommendations.
We help address identified risks. This could include cloud setup, network segmentation, API protection, or OTA redesign. During hardening, we work on firmware security (IoT) and devices, configure IoT device identity management, document new rules, and update processes.
To verify that your system has become more secure, we conduct technical tests, including IoT penetration testing. We also analyze logs, channels, and device behavior. To ensure compliance alignment and help you meet required standards without unnecessary bureaucracy, we prepare audit materials.
Security is a process: we update firmware, patch vulnerabilities, and validate configurations. We provide IoT vulnerability management, monitor regulatory changes, and help organizations adapt to new standards. This way, we ensure your business remains resilient and ready for audits.
Benefits of making your IoT network secure and compliant
Fewer incidents, less downtime
We conduct IoT risk assessments and manage IoT vulnerabilities by patching them in firmware, networks, the cloud, and support scenarios.
Expedited compliance and auditing
We help organizations build regulatory IoT compliance by covering IEC 62443, GDPR, HIPAA, and SOC 2.
A more secure launch of new IoT products
We conduct IoT threat modeling and apply best practices to strengthen IoT firmware security and the pre-release update process.
A clear picture of risks for management
We translate technical findings into the language of costs, penalties, and time-to-market and demonstrate how IoT cybersecurity impacts product and market plans.
Reduced costs for rework and firewall fixes
We build IoT security into the architecture from the outset, reducing the cost of changes and the risk of delays before certification.
Increased trust from customers and partners
Visible control over IoT data encryption and incidents builds trust and eases access for large customers and regulated industries.
Security is a shared responsibility
IoT security requires a clear division of roles. We transparently document which tasks SumatoSoft handles, which remain your team’s responsibility, and what is covered by the cloud provider.
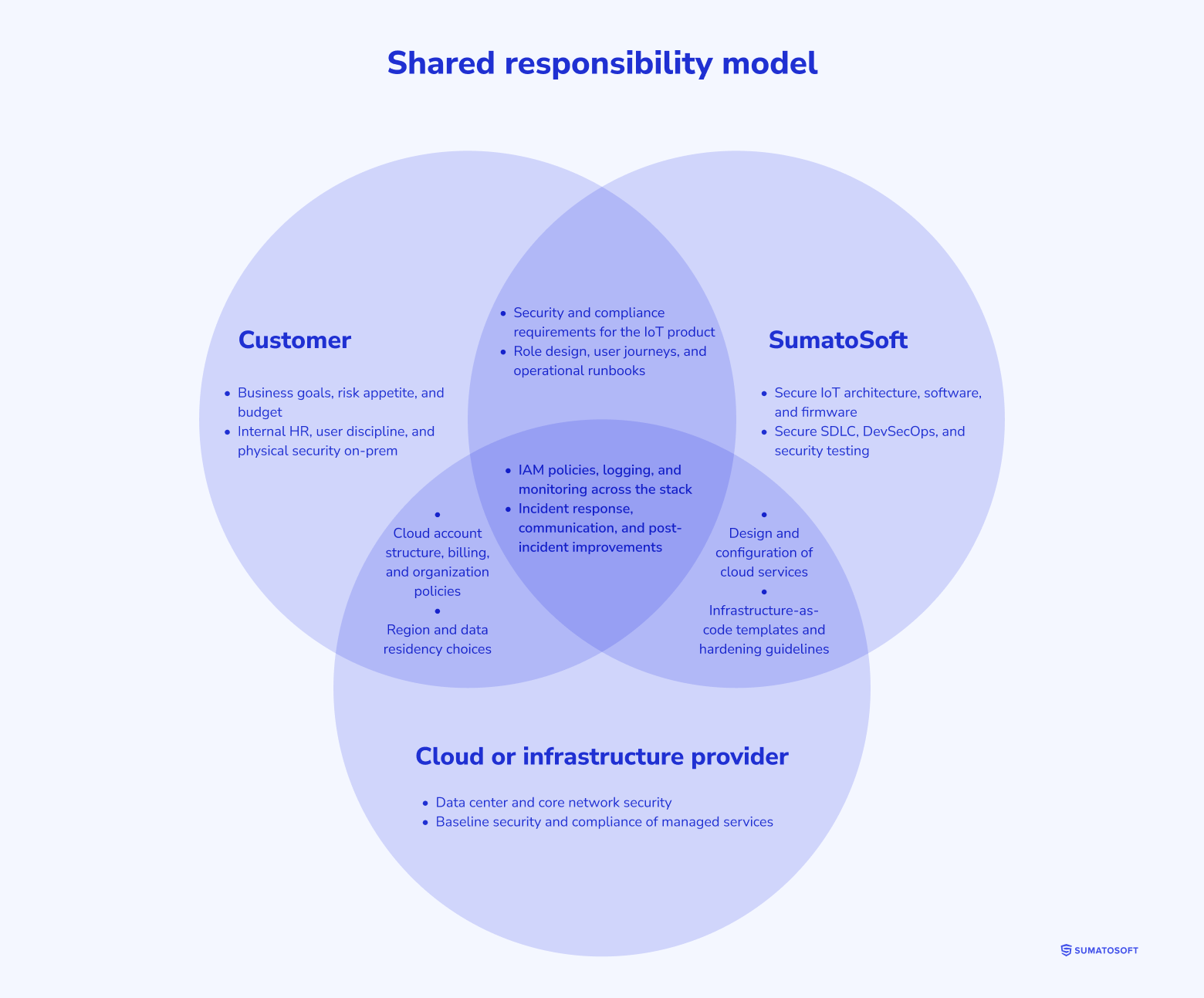

Collaboration models
Security assessment and roadmap: Fixed scope
This model is a popular first step.
Suitable for companies that need:
- An audit of their current IoT system
- IoT risk assessment
- IoT threat modeling
- A remediation and compliance plan.
What we provide:
- Vulnerability report
- Architecture and hardening recommendations
- Risk map
- Implementation plan for IEC 62443, GDPR, HIPAA, and other compliance.
Security improvements and hardening: Time & Material
This model is suitable when the scope of changes cannot be determined in advance.
You choose the areas:
- Cloud
- Network
- Firmware
- Access management
- IoT data protection
- OTA, and DevSecOps.
We strengthen the system step by step, quickly address critical risks, and refine the architecture.
Dedicated security team
A small, dedicated team for your IoT scenarios. This model is suitable for companies with a large IoT base or complex infrastructure (medtech, manufacturing, utilities).
This model includes:
- Continuous monitoring
- IoT vulnerability management
- IoT penetration testing cycles
- Compliance training
- Firmware updates and configuration verification.
Security consulting and compliance support
Long-term support without development from scratch. Suitable when your team makes changes themselves but needs expertise.
We help:
- Build security processes
- Pass partner or regulatory screening
- Implement IAM for devices and users
- Configure secure DevSecOps
- Prepare policies, procedures, and artifacts for audits.
For 13+ years, we have proudly taken responsibility for your IoT projects!
Awards & Recognitions
Frequently asked questions
What does an IoT risk assessment include?
We assess devices, networks, clouds, and APIs, then evaluate risks, create a threat map, and identify critical points. This helps us understand what needs to be addressed first. An audit is the first step to truly securing the IoT.
How does IoT threat modeling work?
We describe attack scenarios on devices, gateways, communication channels, and services. Then, we examine what could go wrong and how to stop it. The threat model helps prioritize and mitigate incident risk.
How do you ensure IoT firmware security and best practices for its updates?
We include signature verification, bootloader protection, and integrity control. The OTA process is encrypted, rollback-enabled, and keys are securely stored. This ensures that firmware cannot be tampered with, even with physical access.
How do you manage the identity of IoT devices?
Each device receives its own key or certificate. We configure registration, rotation, and revocation. Only trusted devices can connect to the network and services.
How do you ensure your Clients comply with industry regulations?
We analyze the system and compare it against the applicable regulations, including IEC 62443, GDPR, HIPAA, NIST, FDA, and others. Then, we prepare a changelog and artifacts for audit.
Let’s start
If you have any questions, email us info@sumatosoft.com