Best Fintech Software Development Companies (2026 Shortlist)

- Fintech vendors should be judged on production reality: money flows expose weak systems fast.
- Most fintech failures come from back-end logic and integrations.
- Strong vendors design for messy edge cases: retries, duplicates, reversals, delayed statuses, disputes.
- A proper ledger and audit trail are core to trust, reconciliation, and defensible balances.
- Compliance is shared: legal sets rules, engineering implements controls, and the Client remains accountable.
- Integrations “run the product,” so idempotency, state models, and failure handling must be first-class.
- Operational readiness is part of delivery: observability, incident response, runbooks, and DR where needed.
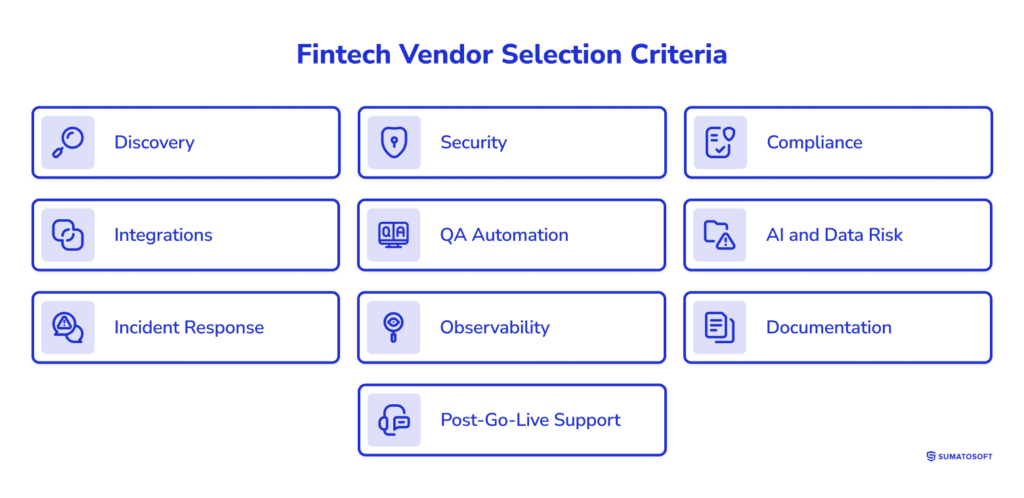
- Vendor selection should use clear criteria: Discovery, Security, Compliance, Integrations, QA automation, AI/data risk, Incident response, Observability, Documentation, and post-go-live support.
- Costs and timelines depend on integrations and compliance scope more than on screens and features.
- Regulation and infrastructure changes in 2026+ will add requirements to fintech roadmaps, particularly around resilience, reporting, and post-trade timelines.
Fintech exposes weak software faster than almost any other category. In most products, a bug is an inconvenience. In fintech, the same bug becomes a balance dispute, a support escalation, an audit question, or a partner review you fail to pass. And the problems usually come from the parts behind the UI: accounting logic that can’t explain itself, integrations that behave unpredictably, and controls that were planned “after the MVP.”
That’s why choosing a fintech development vendor is a risky decision. The best teams build around the assumption that real life will be messy: payments will be delayed, providers will send duplicates, statuses will change retroactively, and production incidents will require quick answers. They design systems that remain correct, traceable, and operable under pressure.
In this article, we break down what “good” looks like using vendor selection criteria that reflect fintech production needs, i.e., discovery, security, compliance, integrations, QA automation, incident response, observability, documentation, and post-go-live support, and then share a shortlist of vendors that appear strong on those dimensions based on public information.
Our fintech vendor selection criteria
Before you shortlist vendors, decide what “good” means for your fintech build. Many firms can ship features. Fewer can ship a product that remains accurate under real-world money flows, third-party dependencies, and audit pressure.
We have a strict methodology that we use when writing any article on top companies, such as top offshore development companies.
The criteria we considered when creating the shortlist of vendors are below:
- Discovery process,
- Security and compliance to avoid costly redesigns,
- Integrations to handle real-world provider behavior,
- QA automation to keep regressions under control.
We also address AI and data risk when models or sensitive data are involved, as well as incident response, observability, and documentation. These basics determine how fast you recover when something breaks. Finally, post-go-live support matters because fintech work doesn’t end at launch; production is where the real cost of weak delivery shows up.
Using these criteria, we reviewed a range of fintech development providers. We looked past generic claims to the parts that matter in production: how teams scope work, build controls, manage integrations, and support systems after launch. The list below is a shortlist of companies that, based on their public positioning and service offering, appear well-suited for fintech delivery and worth considering as a starting point for vendor selection.
Top fintech software development companies
Below is our shortlist based on publicly available information about their fintech offerings, delivery approach, and services.
SumatoSoft

What they do: Custom software product development across industries, including finance. They develop fintech solutions, including wealth management software, compliance and reporting tools, payment processing systems, and related tech.
Key services: Full-cycle custom development, product development, web and mobile, IT staff augmentation, dedicated teams.
Competitive advantages:
- ISO 27001 and ISO 9001 are listed among trust signals.
- Emphasis on structured delivery and long-term cooperation metrics.
Euvic

What they do: Euvic is positioned as an enterprise-grade software development and IT services provider. For fintech buyers, the relevant angle is delivery in environments where integrations, security controls, auditability, and operational stability matter as much as feature output.
Key services: Full-cycle software development; systems integration; web and mobile development; QA and test automation; cloud/DevOps; data engineering and AI. These capabilities align well with fintech builds that depend on external providers (KYC/AML, PSPs, banking APIs) and require predictable production operations.
Competitive advantages:
- Enterprise delivery model: structured execution, documentation, and change control practices that fintech teams usually need for audits and partner reviews.
- Strong quality emphasis via QA and automation offerings (applicable for regression-heavy fintech products).
- Visible third-party credibility signal via Client reviews/ratings on Clutch.
Vention

What they do: Vention positions itself as a financial/fintech software development company building banking, lending, insurance, and related solutions.
Key services: Financial software development, integration, modernization, and compliance-aware delivery across industries (including PCI-DSS listed among fintech standards).
Competitive advantages:
- Breadth across fintech verticals (banking, lending/credit, insurance).
Intersog

What they do: Intersog positions itself as a custom software development partner with consulting, product engineering, and AI capabilities. For fintech, the key value lies in building production-ready systems that handle sensitive data, complex workflows, and reliability requirements.
Key services: Product discovery and consulting; custom software development; web/mobile development; cloud and DevOps; QA; data/AI. These are often relevant for fintech products that require robust admin tooling, integration-heavy backends, and operational readiness.
Competitive advantages:
- Emphasis on discovery and consulting, which helps when regulation, partner rules, and risk controls constrain fintech requirements.
- Broad delivery footprint (nearshore/offshore options) and experience metrics they publish, useful if you need team scaling without losing process discipline.
- Capability coverage across engineering + data/AI, which matters for fraud signals, monitoring, and reporting pipelines in many fintech models.
Relevant

What they do: Relevant offers fintech software development services for financial institutions, banks, and fintech product teams.
Key services: Fintech consulting, development, mobile development, modernization, PoC/MVP, AI-enabled fintech, white-label fintech development.
Competitive advantages:
- Compliance and security are planned upfront. Their delivery flow explicitly includes “compliance and security planning” early in the lifecycle, not as a late add-on.
- Breadth across fintech system types. They publicly list work areas, including risk and compliance management software, fraud detection, digital wallets, banking software, and trade/investment management systems.
SDK.finance

What they do: A fintech platform product (not just services) built around a ledger/transactional core, positioned for banking/payment products.
Key services: Platform capabilities like real-time transaction recording, multi-currency support, reconciliation tooling, and an API-driven approach.
Competitive advantages:
- Source code license positioning (control and customization without vendor lock-in, per their materials).
Trio.dev

What they do: Trio.dev focuses on outsourcing to fintech teams, offering dedicated team models and compliance-aware delivery messaging.
Key services: Dedicated teams, fintech-oriented delivery support.
Competitive advantages:
- Clear positioning toward startups/scaleups and engineering leaders building fintech products.
Orangesoft

What they do: Fintech app development services with a product-development framing (concept to scale-up), plus security testing and modernization.
Key services: Web/mobile fintech apps, security audits/testing, consulting, modernization/support; lists fintech subdomains like payments, wealth/investment, personal finance, crypto wallets.
Competitive advantages:
- Publishes a detailed delivery process and emphasizes security/compliance and scalability as core concerns.
Innowise Group
What they do: Innowise Group positions itself as a fintech development company delivering custom fintech solutions with operational support and documentation practices.
Key services: Fintech development, plus broader software development and consulting.
Competitive advantages:
- Compliance-aware fintech delivery (built into their offering). They explicitly state alignment with PSD2, PCI DSS, and GDPR, and describe the implementation of automated KYC/AML and transaction monitoring as part of fintech builds.
- Strong QA capacity suited to regulated fintech releases. They emphasize ISTQB-certified QA and cover security testing and automated test coverage, including validation against fintech-relevant rules such as PCI DSS, AML, and KYC.
SoluLab

What they do: Fintech app development with a strong emphasis on banking, wallets, lending, and compliance-aligned delivery.
Key services: Banking apps, wallet apps, lending platforms, AI-powered fintech, RegTech/compliance engineering, white-label fintech platforms.
Competitive advantages:
- Apparent breadth across fintech product types and compliance themes.
dashdevs

What they do: Fintech product development with end-to-end mobile finance app delivery and a heavy focus on integrations (including open banking APIs).
Key services: Fintech app development, banking/open-banking API integrations, third-party integrations, native + cross-platform development, plus fintech feature modules (auth, fraud detection, wallets, analytics).
Competitive advantages:
- Published experience/app volume claims, and a detailed feature-level view of fintech builds.
Benefits of partnering with a fintech software development company
In fintech, almost all key issues arise in product accounting: what exactly happened to the money, when, on what basis, and how to prove it to the Client, partner, auditor, bank, or regulator later.
Therefore, fintech development differs from “regular” development not in the interface style or even the technology set. It differs in that you continually build a system around trust in the balance, transaction history, fee accuracy, and assurance that a payment won’t disappear “between statuses.”
Benefit 1: Expertise saves from errors
A good fintech development team is helpful because they anticipate common failures in advance, which almost inevitably occur in a product that handles money: payments are delayed, webhooks are duplicated, providers change statuses retroactively, and more. A user cancels a transaction when it’s “almost complete.” The system repeats the request after a timeout, creating a duplicate. Support needs to resolve the issue without manual intervention and without risking further issues.
The difference between an experienced and an inexperienced team is usually that the former projects these situations as usual. The latter discovers them in production and begins patching them up.
Benefit 2: Accounting for money and statuses is a separate product layer
If your product needs to maintain balances, process write-offs, make deductions, distribute commissions, and handle transactions or loan settlements, you have a task that a single database table can’t address.
You’ll need an accounting layer. It’s often called a ledger: a journal of transactions and the rules by which they are recorded, converted into a balance, and preserved as history. Ledger is used to ensure that the balance reflects transparent records. Everything else is built around this layer: reconciliation, disputed transactions, returns, reports, investigations, and audits.
Benefit 3: Regulations and standards influence system design
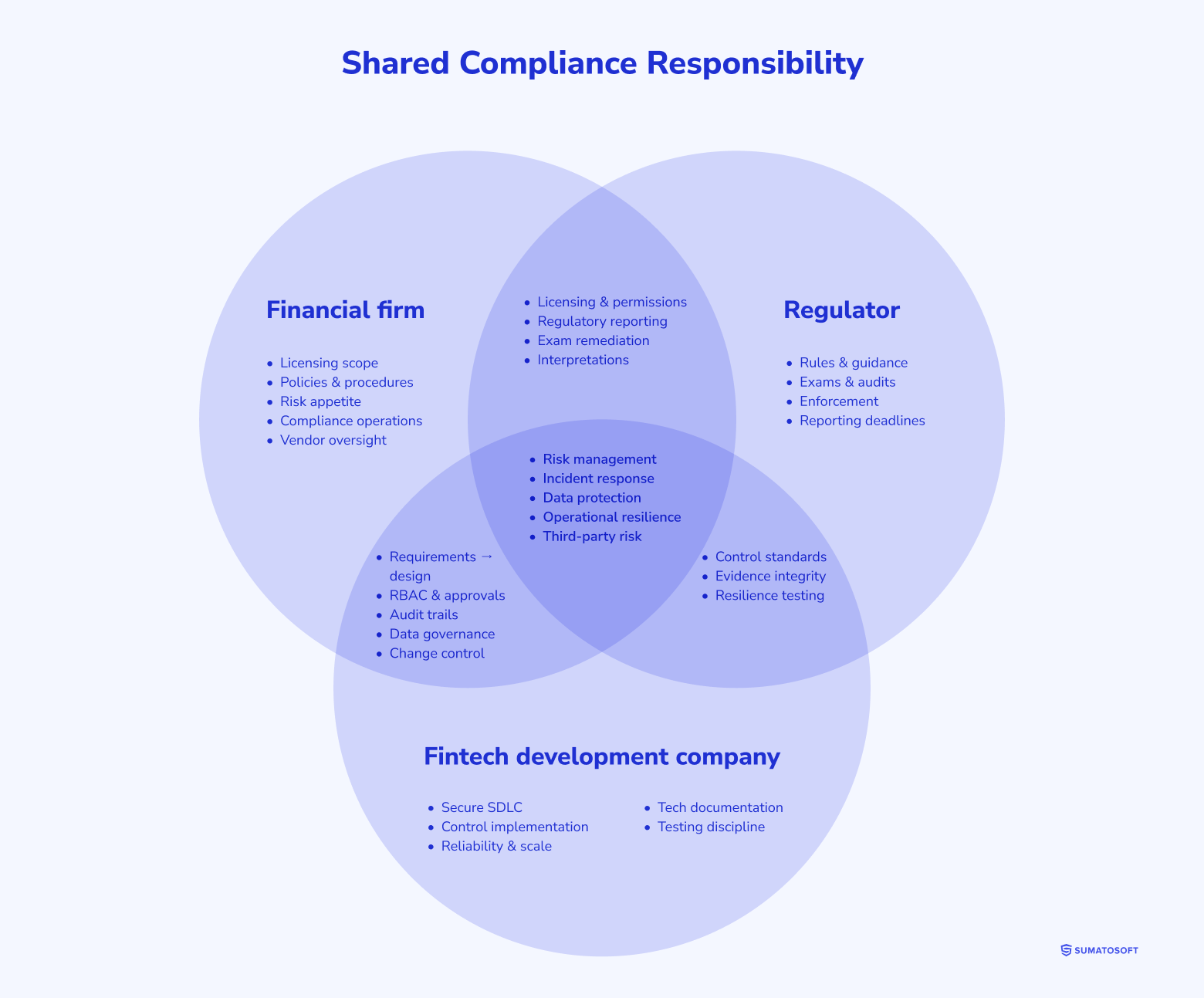
It’s essential to be clear: a contractor doesn’t replace your lawyer or compliance officer. However, the contractor must understand that regulatory requirements aren’t merely sections of the documentation; they are restrictions on how the product is designed.
For example:
- If audit trails are needed, you design an immutable record of history and a delineation of rights.
- If there are data requirements, you decide in advance where personal data is stored.
- How consents are structured, how deletion works, and what remains in the accounting system.
- If the product depends on contractors and the cloud, you build a process for vendor risk management and failure preparedness, as large Clients and audits expect.
Standards define a separate class of requirements. PCI DSS is essential if you work with credit card data. ISO 27001 affects process and access control more than a specific button, but it’s also part of “product trust”: how you manage secrets, rights, incidents, and changes.
Certifications are a sign of discipline: rules, process owners, repeatability, and change control.
Benefit 4: Integrations are the main source of complexity
Most fintech products rely on integrations: KYC/AML, banks and payment providers, open banking, market data, reporting systems, anti-fraud, and notifications. And almost every integration brings its own status and error model.
An experienced team does two things that make your product’s lifecycle significantly easier:
- Designing integrations so that an external service failure doesn’t result in data loss or a “half-freezing” state,
- Make idempotency and duplicate handling part of the contract.
This is what separates a stable payment or trading product from one that’s vulnerable to load and peaks. To assess the role of integration aspect in final software development costs, check out our guide on software outsourcing costs.
Benefit 5: Production and support are part of development
General software development providers might underestimate the cost of operational support in fintech. When a product is small, it seems like “we’ll figure it out.” As operations volume grows, more partners are added, reporting, and SLA requirements increase, and support becomes a constant source of investigation.
When a team plans production, they develop appropriate product features: monitoring infrastructure and business events; alerts that detect workflow deviations; logs to reconstruct the chain of operations; runbooks for support; and a recovery plan in case of failure.
This directly impacts costs because each investigation requires the team to spend hours and carries a risk of a wrong decision.
Benefit 6: High-quality design in fintech directly impacts revenue
In fintech, design is about how quickly end users can access funds and how often they encounter friction. For businesses, good UX reduces losses at the most expensive stages: onboarding, verification, first deposit, first trade, and first withdrawal. If people get stuck on KYC or don’t understand the transfer status, you’re paying twice: you lose conversions and increase support workload.
There’s also a more direct impact on revenue. When users see clear fees, understandable limits, and transparent statuses, they’re more likely to complete the transaction. When the confirmation screen is straightforward, there are fewer cancellations at the last step. When errors are explained clearly, there are fewer abandoned attempts and repeated tickets.
Design also impacts risk. Poor wording, unintelligible switches, and “hidden” settings in the admin panel lead to operator errors and incidents.
This makes design in fintech another vital part for end-users’ clarity, trust, and conversion.
What makes a fintech software development company great?
A great fintech software development company is great for one reason: it builds software that stays correct and explainable when real money starts moving.
But how to identify such a company? We prepare a brief vendor evaluation checklist for you – feel free to download it.

Many vendors can sound convincing: they’ll talk about security, compliance, and speed. Those things matter, but they’re not the test. The test comes when reality hits: reversals after “success,” duplicate callbacks, new KYC statuses, balance disputes, partner audits, and production incidents that require immediate answers.
A strong fintech team designs for those scenarios as the normal case. That’s what separates fintech delivery from generic software delivery.
#1: Fintech development teams treat money as a system
Many teams start by storing the balance and updating it with each operation.
It works until it doesn’t: until an operation is duplicated, until an operation is partial, until an operation needs to be reversed, or until you need to explain why the balance is what it is.
Strong fintech teams build an accounting layer that can answer that question. They design around transaction records, clear state changes, and traceable fees. When something goes wrong, you can reconstruct the story without guessing. And when an auditor or a partner asks how funds move, you can show the logic.
#2: Fintech developers build for scrutiny before they build for scale
Fintech products live under a spotlight that many software products never face: your users expect correctness, your partners expect controls, and your enterprise prospects expect evidence. Regulators expect discipline, even if they’re not in the room yet.
Great fintech vendors internalize that early. They design for auditability as part of the product by implementing access rules, logging actions, defining approval paths, and considering what needs to be retained, who can see it, and how to prove it later.
This is also where certifications become relevant. If a company holds ISO 27001 certification, it often means they’ve formalized their approach to managing security risks and access. If PCI DSS is involved, it imposes strict boundaries on card data environments. None of this replaces strong engineering, but it changes how consistently a team works.
#3: Integrations run the product
Fintech is rarely a self-contained system. After a vendor builds a product, you operate within a network of KYC and AML vendors, payment providers, banks, open banking APIs, market data sources, and reporting services.
If you want a real-world reminder that “integrations run the product,” look at the Flash Crash on May 6, 2010. In minutes, U.S. equities and ETFs saw extreme price swings, and the market snapped back almost as fast.
The joint SEC–CFTC review traced the trigger to a large automated sell program in the E-Mini S&P 500 futures: 75,000 contracts, about $4.1 billion, executed with a volume-based algorithm that did not factor in price. Liquidity was already thin. As selling pressure hit futures, stress spilled into related markets through arbitrage and cross-venue routing.
What matters here for product builders is the mechanics. Modern markets are a mesh of venues, feeds, and shared dependencies. When one part destabilizes, downstream systems inherit the mess: inconsistent states, delayed updates, and “impossible” prints that still need to be processed, explained, and, in some cases, corrected. The SEC described trades at absurdly low prices in some instruments, alongside sharp swings in ETFs.
For fintech platforms that rely on market plumbing, such as brokerage, trading, and portfolio tools, this is the lesson. Your product is only as stable as its integration layer: how you ingest data, reconcile conflicts, handle venue pauses, and keep user-facing state coherent when the outside world stops behaving as expected.
If a vendor talks about integrations as “just connecting APIs,” it’s usually a sign they haven’t paid for mistakes yet.
#4: Your fintech vendor must know what compliance can and can’t do for you
A serious fintech vendor won’t promise to “make you compliant.” Compliance doesn’t work like that. Your legal and compliance owners define the obligations. Engineering makes those obligations real in product behavior, data flows, access rules, and evidence.
What you’re buying from a strong vendor is the ability to translate regulatory language into system design without surprises later. Compliance is shared, but liability isn’t.
Regulators generally don’t care why a control failed. They care that it failed, and who is responsible for it. And the broker-dealer world is a clean example here. FINRA Rule 3110 makes the member responsible for supervision through a reasonably designed supervisory system and written procedures. And FINRA Rule 4370 requires a business continuity plan that covers, among other things, data backup/recovery and “all mission-critical systems.”
For example, in the Robinhood case, FINRA found that the firm outsourced key technology work to its parent company but did not reasonably supervise those outsourced activities, and that its BCP was not reasonably designed to cover technology-related emergencies and mission-critical systems.
You don’t need to be a broker-dealer for the lesson to apply: outsourcing doesn’t remove your obligation to control the outcome. Regulation becomes software requirements faster than most teams expect, but many founders still treat compliance as a checklist at launch. In practice, it quickly becomes product requirements you can’t patch with a few policy pages.
Here are examples you can map directly to engineering work:
| Regulation or rule | What it turns into in software |
|---|---|
| FINRA Rule 4370 (BCP) | Disaster recovery planning, defined “mission-critical systems,” backup/restore tests, and documented procedures. |
| FINRA Rule 3110 (Supervision) | Clear ownership of controls, written procedures, review workflows, and supervision of outsourced work. |
| NYDFS 3 NYCRR 504 (Transaction monitoring and sanctions filtering) | Monitoring rules, alert queues, case management, and evidence to support annual certification. |
| NYDFS 23 NYCRR 500.17 (Cyber incident notice) | Incident detection + classification, reporting workflow, and ability to notify within 72 hours. |
| GDPR Article 33 (Breach notice) | Breach response playbook, audit-ready records, and ability to notify within 72 hours. |
| PCI DSS (Card data environments) | Scope control, segmentation, logging, vendor responsibility split, and proof of compliance for third parties. |
This is why “we’ll handle compliance later” is expensive. By the time you discover you need immutable audit trails, stricter access controls, or better incident reporting, those choices are already baked into architecture.
Case Study: Compliance Work Outsourced Without Oversight
NYDFS fined Coinbase $100M for serious gaps in its AML compliance program. Coinbase agreed to pay a $50M civil penalty, spend another $50M over two years to remediate AML controls, and accept a NYDFS-selected independent monitor.
Сore operational issues of Coinbase:
- Weak risk-based KYC
- Compliance alerts piled up
- An attempt to clear the backlog with contractors without proper oversight.
That breakdown led to downstream failures:
- Late SAR filings
- Weak ongoing sanctions/PEP screening
- A missed 72-hour cyber incident notice requirement under NYDFS Part 500.
TL;DR lesson: if compliance doesn’t scale with growth, it turns into backlogs, missed deadlines, and regulator-imposed remediation. Outsourcing compliance work doesn’t reduce responsibility, it adds another layer you must supervise.
#5 Fintech development experts ship like people who will be on call
Most vendors can provide a feature list, but the better ones deliver a turnkey solution.
This becomes obvious the first time something breaks in production. Support needs an answer, and “we’re investigating” is an uncertainty that users don’t tolerate around money. They also don’t care whose fault it is.
Strong fintech teams build with that reality in mind. They don’t treat operations as a handoff after launch. They design it into the product during development.
#6 Fintech experts can explain tradeoffs without hiding behind slogans
Fintech is a chain of decisions where every option has a cost.
Do you build a core ledger or adopt a platform? Do you maintain a single ledger or separate ledgers by product line? Do you process events in real time or accept eventual consistency? Do you tighten onboarding controls or optimize for conversion? Do you show “instant” balances when settlement is still pending?
Weak vendors make these choices sound easy because they want to sell you certainty and promise you speed, while skipping the complex parts of the pitch.
Strong vendors make trade-offs explicit and tie them back to operations and compliance.
Main services offered by fintech software development companies
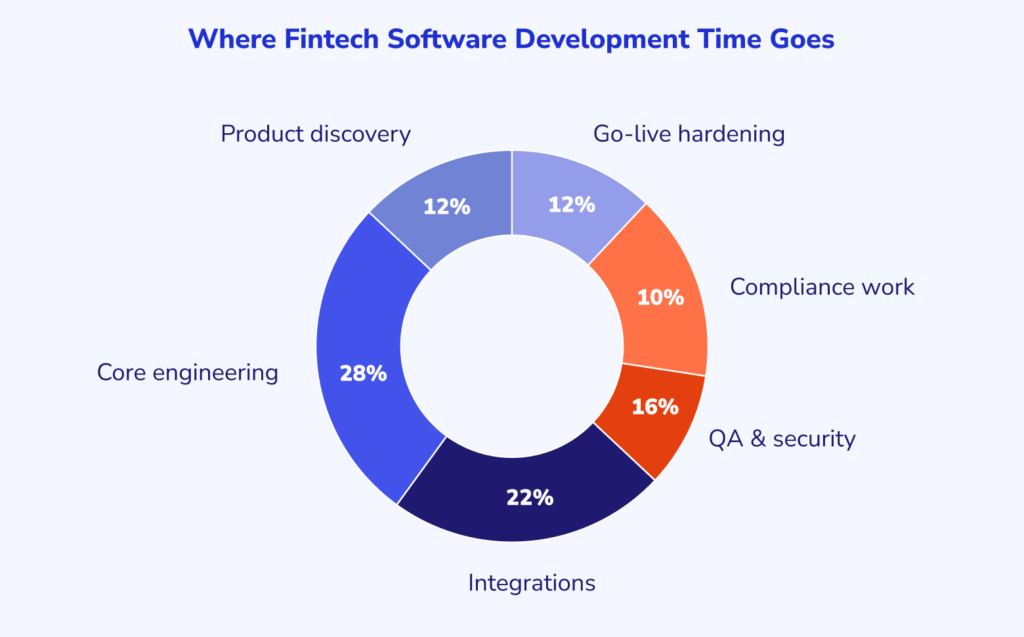
These categories cover most fintech engagements:
- Product discovery and scoping
- UI/UX + design systems
- Core fintech engineering
- Integrations
- Data engineering and analytics
- QA and test automation
- DevOps/SRE
- Ongoing support and modernization
How to choose the right fintech software development company
A selection flow that works for both startups and enterprises:
Step 1: Define your fintech category and regulatory surface area
Payments/wallets, lending, wealth/trading, insurance, and banking each have different integration and control needs.
Step 2: Pick your build approach
- Custom build (maximum control, longer ramp)
- Platform-based build (faster launch, constraints depending on licensing/model).
Step 3: Ask for evidence
- Architecture samples (sanitized), delivery artifacts, incident postmortem examples, test strategy, and a real integration story.
Step 4: Run a paid discovery
Require: backlog, architecture options, integration plan, security plan, milestone schedule.
Step 5: Confirm operational readiness
Monitoring/alerting, release strategy, DR, and ownership boundaries.
7 future trends in fintech software development (2026 and beyond)
These are trends that directly change what fintech software teams must build. Taking them into account when choosing a vendor is advisable, as well as trends in web outsourcing.
Trend #1: EU AI Act: enforceable rules start in 2026
From 2 August 2026, the bulk of the EU AI Act will take effect, including rules for many high-risk AI systems and the Act’s transparency requirements.
For fintech teams, this matters if you use AI for creditworthiness/credit scoring, fraud decisioning, customer risk profiling, or automated monitoring workflows. You should expect more work around:
- Model risk management and documented controls,
- Data governance and traceability,
- Logging and human oversight,
- Audit-ready technical documentation.
There is also an extended transition period for high-risk AI embedded in certain regulated products, valid until 2 August 2027.
Trend #2: EU payments reset: PSD3 + PSR (new fraud and transparency expectations)
The EU’s PSD2 review has progressed to a new framework (PSD3 and a Payment Services Regulation). A provisional political agreement between the Council and Parliament was reached on 27 November 2025.
While final application dates depend on formal adoption and transition periods, you should expect stronger anti-fraud measures, greater transparency around fees, and tighter rules governing payment flows.
Trend #3: Instant Payments Regulation: deadlines continue through 2027–2028
Even if your core product isn’t “instant payments,” these deadlines affect payment rails, fraud controls, and name/IBAN verification logic across PSPs:
- January 9, 2027: receiving instant euro payments and “equality of charges” for non-euro area member states.
- April 9, 2027 / July 9, 2027: obligations extend to payment institutions and e-money institutions (with different dates for euro vs non-euro areas).
- June 9, 2028: requirements apply to certain accounts denominated in national currency that are outside business hours in non-euro-area member states.
Trend #4: EU post-trade compression: T+1 in 2027, with build work to start earlier.
The EU is moving from T+2 to T+1 settlement by October 11, 2027. That date seems far off, but the software impact occurs earlier because post-trade workflows need re-engineering. ESMA has already framed operational readiness work, such as:
- Same-day allocations and settlement instructions,
- Machine-readable allocation/confirmation formats,
- Features like hold/release, auto-partial settlement, and auto-collateralisation.
If you build brokerage/trading or any OMS/post-trade tooling, this becomes a roadmap item.
Trend #5: DORA spillover: more scrutiny on ICT vendors and third-party concentration risk
DORA is already in force, but its effects will continue to compound. EU authorities are moving toward direct oversight of “critical” ICT providers used by financial firms, resulting in stricter requirements for vendor governance, contract terms, and resilience evidence.
In development, fintech teams should expect more work around:
- Third-party registers and dependency mapping,
- Exit and substitution plans,
- Resilience testing and evidence that stands up in audits.
Trend #6: AMLA ramp-up toward 2028 direct supervision
The EU’s AMLA is building toward direct supervision from 2028. In 2026, AMLA’s own timeline highlights the ramp-up of IT business services and assessment of future IT needs, with entity selection in 2027.
Translation for product development teams: AML expectations will become more harmonized, and “evidence quality” (case management, audit trails, explainability of decisions, data lineage) will matter more.
Trend #7: US open banking: likely a 2026+ driver, but legally unstable
US “open banking” (CFPB Section 1033) had an implementation timeline where the largest providers would have needed to comply starting April 2026, but compliance dates have been stayed, and the rule has faced court action and revision pressure.
Even with uncertainty, product teams should plan for stronger consent, data-sharing controls, and API governance, because Client expectations are moving in that direction.
FAQs
1) What services does a fintech software development company provide?
Typical services a fintech development company provides are discovery, UI/UX design, core fintech engineering, integrations (KYC/AML, PSPs, banking rails), QA automation, DevOps/SRE, and support.
2) How much does fintech app development cost?
A fintech app built by US teams typically costs $80k–$200k for an MVP, $200k–$600k for a market-ready build, and $400k–$1M+ for complex platforms. In Europe, budgets are usually lower: roughly $60k–$160k (Western Europe/UK) or $40k–$120k (Central/Eastern Europe) for an MVP, scaling to $350k–$900k+ for complex systems, depending on integrations and compliance scope.
3) How long does it take to build a fintech MVP?
A fintech MVP typically takes 12–20 weeks (about 3–5 months) when it includes one core flow, 1–2 key integrations (e.g., KYC and payments), and a basic admin panel. If you add multiple providers, complex risk rules, or stricter compliance evidence (audit trails, reporting), plan 20–32 weeks (about 5–8 months).
4) Do fintech apps need PCI DSS compliance?
If you store, process, or transmit cardholder data, then yes, PCI DSS requirements apply to your card data environment and processes.
5) Can a fintech development company integrate KYC/AML and fraud detection tools?
Yes. Most fintech builds require KYC onboarding, AML monitoring hooks, and audit-friendly event logs. The key is designing clean integration boundaries and failure handling.
6) Who owns the source code after development?
In custom development, ownership is usually transferred to the Client under the contract (confirm explicitly). Some vendors state this directly in their FAQs and policies; always validate in legal terms.
7) What should I ask a fintech vendor before signing?
Ask for: a paid discovery deliverable list, security practices, SDLC controls, incident response approach, architecture options, and examples of similar integrations (sanitized).
8) Can SumatoSoft modernize an existing fintech product built by another vendor?
Yes. We specialize in taking over projects, refactoring and re-architecting, and stabilizing production systems.
Let’s start
If you have any questions, email us info@sumatosoft.com