Guide: 10 Methods to Manage Threats in Mobile Banking Security

Mobile banking applications operate in a high-risk environment by default.
Processing financial transactions, dealing with highly sensitive personal data, vulnerability to social-engineering attacks, network-level threats, and much more. The hardest part here is that even a single breach or mistake undermines customer trust and triggers regulatory and reputational consequences.
I outline the most common mobile banking security threats, explain how they arise, and describe the practical security measures we apply in banking projects to mitigate them. The focus wil be on concrete, implementation-level practices.
Short author bio
Hi, I’m Aleh Kanoika, a Tech Lead at SumatoSoft with over 6 years of experience in mobile banking and financial software development. I specializes in designing secure, scalable architectures for regulated environments and establishing engineering practices that improve code quality and system reliability.
Over the past six years, I have participated in multiple highly regulated projects and even had a pleasure working with complex project from World Bank Group. In this article, I will share my expertise and knowledge of developing secure software solutions
Is mobile banking security really at risk?
Yes. Mobile banking apps are a prime target for cybercriminals. They provide direct access to money, store sensitive personal data, and run on millions of devices with different security conditions. This creates a structurally attractive attack surface.
Industry data confirms this focus.
Zimperium’s Mobile Banking Heists Report (2023) identified 29 malware families targeting over 1,800 mobile banking apps in 61 countries. This reflects sustained, organized attacker activity against mobile banking platforms.
Mobile banking trojans designed to steal credentials and hijack accounts are surging as well.
Research from Kaspersky, a global cybersecurity company best known for antivirus software and threat research, found that in the first half of 2025, detections were almost 4 times higher than in the same period in 2024. This reflects attackers’ ability to distribute malicious code at scale across mobile platforms.
AI-driven social engineering further amplifies the threat. A global survey of financial institutions from Group-IB international security company shows that deepfake voice phishing now causes average losses of about $600,000 per incident, with over 10% of banks reporting individual losses above $1 million.
These trends show that mobile banking security risks stem from both technical weaknesses and user behavior – and are now magnified by automation and AI.
Mobile banking security common threats
Mobile banking threats come from different parts of the system. Most incidents happen when attacker actions, user mistakes, and software weaknesses meet.
For clarity, these threats can be split into three groups:
- Social-engineering threats: attackers persuade users to share access details or confirm payments they did not intend to make.
- Environment-related threats: risks caused by infected phones, altered operating systems, or unsafe networks.
- Application-level threats: flaws in mobile apps, backend systems, or APIs that attackers can use directly.
This split helps because each group needs its own protection methods. Social-engineering threats require measures that reduce the damage from stolen access. Environment-related threats need safe default settings and tolerance to risky device conditions. Application-level threats must be handled through careful system design, clean code, and regular security checks.
The following sections look at each threat group and explain how it affects mobile banking in everyday use.
Group 1: Social-engineering threats
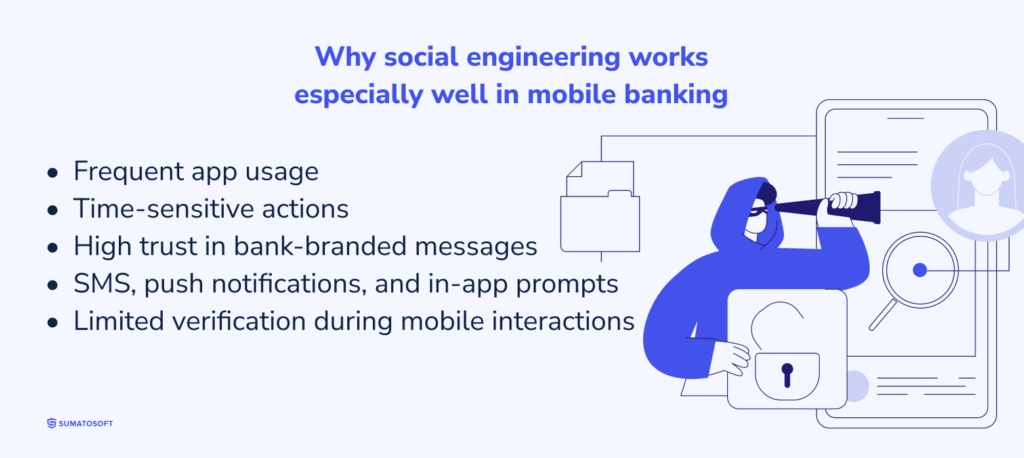
Social-engineering attacks work through people, not code. Attackers do not break into the app. They steer users into opening the door themselves: handing over login data, confirming a payment they never planned, or installing harmful software.
Mobile banking is an easy stage for this. Users check apps often, act in a hurry, and usually trust messages that look “bank-branded.” SMS, push alerts, and in-app prompts give attackers familiar channels to run their tricks.
These attacks cut straight through security layers. Once attackers hold real credentials or a valid approval, even a hardened system can be misused. Defense therefore focuses on limiting the consequences of user missteps rather than expecting users to spot every trick.
1.1 Phishing and smishing
Phishing and smishing are the workhorses of social-engineering attacks in mobile banking. Attackers copy banks or payment services and send messages that create pressure: act now, click here, fix a problem.
Users are led to fake pages or nudged into approving actions they did not intend. With that access, attackers enter accounts directly or pair the stolen data with other attack paths.
Because these attacks depend on persuasion, they cannot be trained away. Real protection comes from making stolen access less useful: strong authentication, payment checks, behavior signals, and tight session controls, discussed later.
The impact of AI on social-engineering attacks
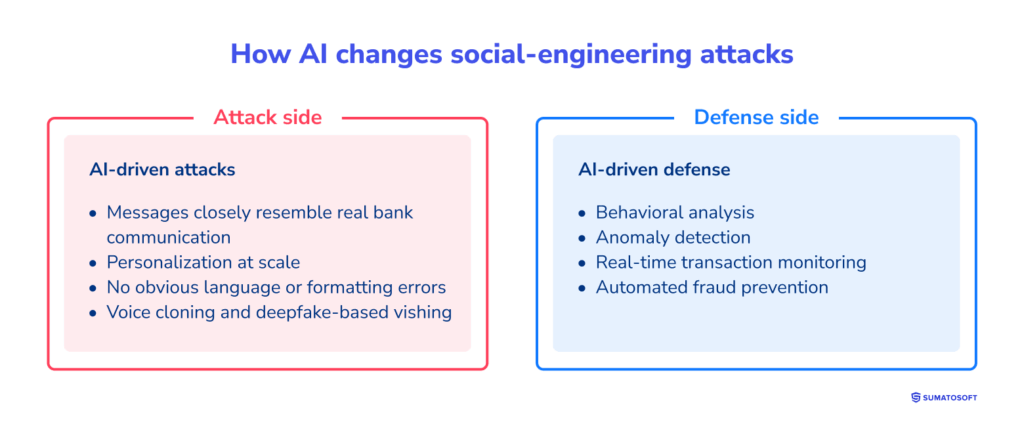
AI has reshaped social-engineering attacks against mobile banking users. Attackers no longer depend on clumsy templates. They use AI to scale deception, tune messages, and adjust wording on the fly.
AI tools generate phishing and smishing messages that closely resemble real bank communication. Tone, structure, and language look familiar. Attackers can now run mass campaigns while keeping a personal feel. Old red flags like bad grammar or generic phrasing no longer work.
AI has also pushed attacks beyond text. Voice cloning and deepfakes are used in vishing to mimic bank staff or trusted contacts. In mobile use, where interactions are short and checks are minimal, these tricks work especially well.
AI is also used for defense. Banks apply machine-learning models to track behavior, spot unusual transactions, and flag risky login flows in real time. These systems reduce damage by stopping fraud before money leaves the account.
This cuts to a simple rule. Social engineering cannot be solved by training alone. Protection depends on adaptive controls: strong authentication, behavior analysis, transaction checks, and automated responses that evolve as AI-driven attacks evolve.
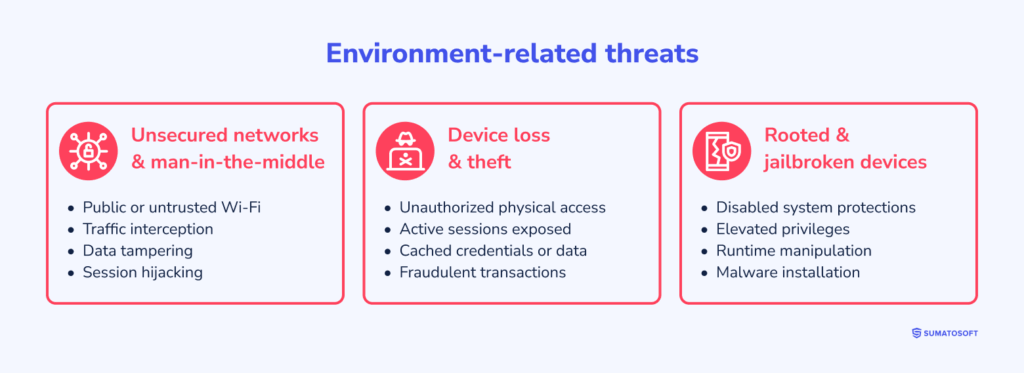
Group 2: Environment-related threats
Even a well-built app can fail if the device or network around it is unsafe.
Environment-related threats come from the setting in which a mobile banking app runs. The problem is not the app logic, but risky surroundings: infected phones, shaky networks, or weak protection at the system level.
These risks never fully disappear. Devices differ, connections change, and users install all kinds of software. A banking app must keep working safely even when conditions are unstable or openly unsafe.
2.1 Unsecured networks and man-in-the-middle attacks
Many users access mobile banking through public or unfamiliar networks, such as open Wi-Fi. In these cases, attackers may try to place themselves between the app and the bank to listen in or alter data.
Encryption helps, yet gaps remain. Trouble starts when certificates are checked loosely, outdated protocols slip through, or inspection tools run on compromised networks. Protection depends on tight transport rules, careful certificate checks, and constant verification that data has not been tampered with.
2.2 Device loss and theft
A missing phone creates instant exposure, especially if screen locks or system safeguards are weak. Anyone holding the device may reach active sessions, cached details, or payment actions.
Risk reduction comes from limiting access at every step. Strong authentication, little or no sensitive data stored on the device, and quick session shutdown when behavior looks odd all reduce damage.
2.3 Rooted and jailbroken devices
Rooted and jailbroken devices remove built-in limits set by the operating system. They give broad access to system internals and make hidden changes easier.
On such devices, attackers can observe app activity, interfere with isolation, or alter how the app runs. Banking apps usually react by spotting elevated privileges and either restricting features or cutting access when the danger becomes too high.
These risks live inside the product. Teams can fix them. If they don’t, small mistakes grow fast.
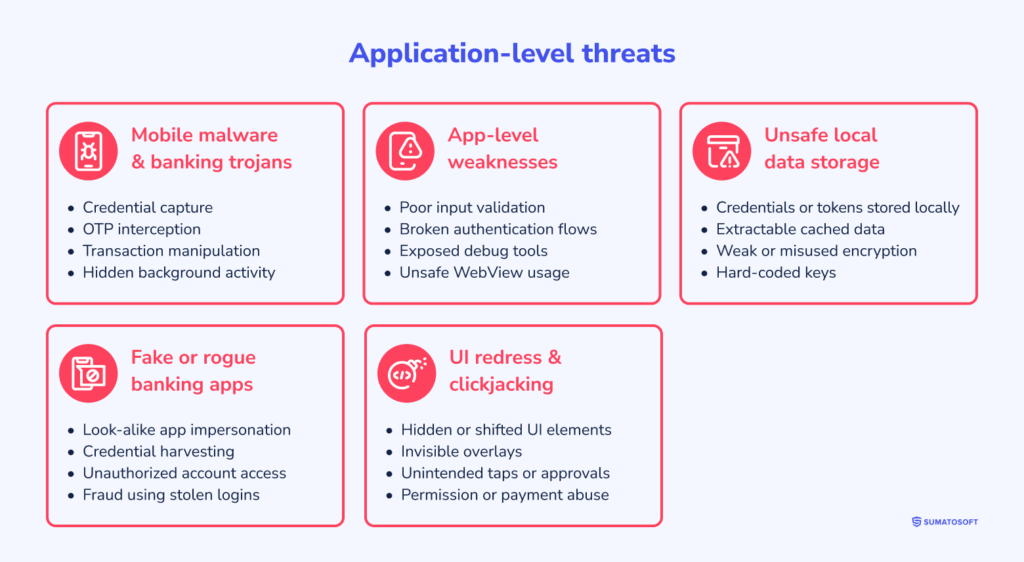
Group 3: Application-level (developer-owned) threats
Application-level threats come from weak spots in the mobile app, backend, or APIs. Attackers hit these paths directly. Unlike user tricks or device issues, these risks sit fully with engineering teams.
In mobile banking, small errors scale quickly. A minor bug can unlock data, weaken controls, or turn limited access into full account takeover. Many attacks rely on these flaws to move deeper once an entry point appears.
3.1 Mobile malware and banking trojans
Banking trojans and mobile malware watch what users do. They grab credentials, intercept one-time codes, and alter transactions while the app runs.
Risk rises when apps expose sensitive data in memory, skip integrity checks, or rely on weak runtime defenses. Protection aims to shrink the value of stolen data and spot strange behavior early, rather than assuming malware can be blocked completely.
3.2 App-level weaknesses
These include poor input checks, fragile login flows, exposed debug tools, or unsafe WebView usage. Such gaps let attackers inject code, skip permission checks, or reach backend systems.
In banking apps, these issues often come from rushed releases, shallow reviews, or reused components with known flaws. Clear coding rules and frequent testing keep these problems from slipping through.
3.3 Unsafe local data storage
To improve speed or usability, apps sometimes keep data on the device. When credentials, tokens, or transaction details are stored carelessly, attackers can pull them from compromised phones or backups.
Danger grows when encryption is misused, keys are hard-wired, or data lingers longer than needed. Safe storage and strict limits on retained data reduce exposure.
3.4 Fake or rogue banking apps
Fake banking apps copy real ones and lure users into handing over access details. Once installed, they work as quiet data collectors for attackers.
App stores help filter these threats, but damage control happens elsewhere. Strong login checks, server-side verification, and transaction validation limit what stolen credentials can do.
3.5 UI redress and clickjacking
UI redress and clickjacking hide or shift interface elements. Users think they tap one thing and approve another.
These attacks abuse weak UI defenses and loose handling of overlays or accessibility features. Prevention depends on careful screen design, platform protections, and checks that user actions match real intent.
How to ensure robust mobile banking security
Before moving to the well-known practices and my personal recommendation, I want to refer to the Cambridge Savings Bank, a US bank with over 185 years of presence on the market. According to its document on security procedures to enhance online protection, the bank uses the following procedures to enhance mobile banking security:
- multi-factor authentication – password and name are usually the first factor, while a one-time password (OTP) or a token sent to a specific user device serves as the second factor;
- a strong password as a requirement – the length from 8 to 24 symbols, combined letters, numbers and symbols;
- dual control – two users together only can initiate fund transfers. One initiates, another approves;
- settings limit – it implies limits to cash withdrawals, transfers or payments;
- activity reporting – it includes transactions, login attempts, activity times, etc.;
- alerts – provide information about transactions that may require the user’s attention.
Learning from the best is always a good practice.
In continuation, there are three categories of measures to examine:
- Core measures – any banking software must implement these measures by default. It’s just pointless to release the app without implementing these mobile banking security measures.
- Recommended measures – some non-obligatory, but highly useful measures.
- Addressing user-driven risks – there are some methods developers can implement to prevent security breaches on the user side. We talk about them here.
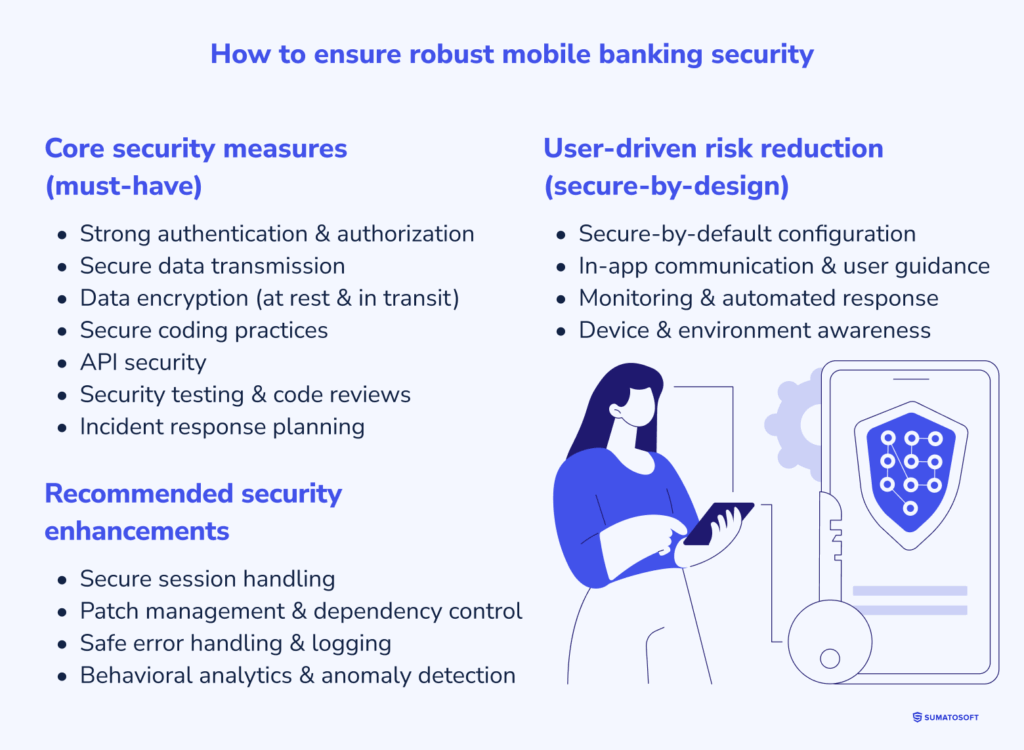
Core security measures (must-have)
Any mobile banking app in a regulated or high-risk setting needs a basic security kit. These controls cover social-engineering, environment-related, and application-level risks described earlier.
Each measure solves part of the problem. Real protection appears when they are applied as a set.
Core #1 Strong authentication and authorization
Strong authentication limits the damage from stolen access. MFA, biometrics, and one-time codes make account takeover harder and more expensive.
Authorization must work the same way everywhere: app, APIs, backend. Role limits and least-privilege rules ensure users and systems can do only what they are allowed to do.
Threats addressed:
- 1.1 Phishing and smishing – measure provides robust defense against attacks aiming to steal login credentials.
- 2.2 Device loss and theft – secures user accounts by requiring authentication factors that a thief is unlikely to possess.
- 3.4 Fake or rogue banking apps – the same as previous: even compromised credentials don’t give access to the personal account.
Core #2 Secure data transmission
All traffic between the app and backend must travel through protected channels. Encryption blocks eavesdropping and tampering on unsafe networks.
Certificate checks and downgrade protection matter, especially on mobile, where public and unmanaged networks are common.
Threats addressed:
- 2.1 Unsecured networks and man-in-the-middle attacks – ciphered intercepted data is almost always useless for any fraud.
- 3.1 Mobile malware and banking trojans – blocking malware from reading or tampering with banking traffic, even on compromised devices.
Core #3 Data encryption at rest and in transit
Encryption protects sensitive data even after a breach. This applies to server storage and to any data kept on the device.
Strong algorithms and proper key handling prevent attackers from reading or extracting data.
Threats addressed:
- 2.2 Device loss and theft – ensures that data on lost or stolen devices cannot be accessed by unauthorized users.
- 2.3 Rooted and jailbroken devices – prevents attackers with elevated device access from reading or extracting protected application data.
- 3.3 Unsafe local data storage – the measure protects stored data from being exploited if the device or server is compromised.
Core #4 Secure coding practices
Clean code reduces the chance of exploitable mistakes. This includes input checks, safe login flows, and protection against common coding errors.
In banking apps, these rules must be clear, shared, and followed by every team.
Threats addressed:
- 3.2 App-level weaknesses – reduces the risk of security flaws within the app that could be exploited by attackers.
- 3.5 UI redress and clickjacking – prevents attackers from manipulating the app’s user interface to deceive users into performing unintended actions.
Core #5 API security
APIs are a main entry point for attackers. They need strict authentication, clear permissions, and request checks.
Rate limits and monitoring help stop automated abuse and attacks from compromised clients.
Threats addressed:
- 3.1 Mobile malware and banking trojans – ensures that data transmitted between the app and server cannot be intercepted or altered.
- 3.2 App-level weaknesses – protects against unauthorized access and data exfiltration by securing endpoints.
Core #6 Security testing and code reviews
Testing finds problems before attackers do. This includes code scanning, runtime testing, penetration tests, and structured reviews.
Security checks should run continuously, not just before release.
Threats addressed:
- 3.1–3.5 All application-level threats are addressed by identifying and allowing for the correction of coding errors that could be exploited.
Core #7 Incident response planning
Even with controls, incidents happen. A response plan defines how issues are spotted, contained, analyzed, and fixed.
Clear steps shorten downtime, limit losses, and support regulatory and customer communication.
An effective plan typically includes:
- Preparation. Training team members and preparing the tools and communication channels needed for an effective response.
- Identification. Detecting and identifying the incident as quickly as possible.
- Containment. Limiting the scope and impact of the incident to prevent further damage.
- Eradication. Finding and eliminating the root cause of the incident, and removing affected systems from the production environment if necessary.
- Recovery. Restoring and returning affected systems and services to a fully operational state.
- Lessons learned. Reviewing and analyzing the incident and the response to it, then using this analysis to strengthen future defenses and response plans.
Threats addressed: Multiple. 1.1–1.2, 2.1–2.3, 3.1–3.5. An incident response plan provides a structured approach to responding to any security incidents, thereby reducing potential damage and recovery time.
An example scenario:
- Identification – a bank discovers unauthorized access to its customer database.
- Containment – the response team identifies the affected systems and databases and isolates them to prevent further damage.
- Eradication – the response team identifies the breach source. In this case, it was an unauthorized access from the remote developer computer that was compromised. They stop the active session from the developer’s computer, remove the access, and run the file check to identify new suspicious files or code changes.
- Recovery – any changed files are recovered from backups, password are changed.
- Lesson learned – the incident is thoroughly reviewed. That results in enhancing the security of remote developer access, improving monitoring and detection systems, conducting additional security training for staff. Additionally, the bank reached its customers to notify them about the data breach.
Recommended security enhancements
These measures go beyond the basics. They cut fraud earlier and spot trouble faster.
Beyond the baseline, mature mobile banking platforms add extra layers that sharpen fraud detection and limit damage. These measures matter most where transaction volume is high or attackers are active.
They do not replace core controls. They reinforce them.
Recommended #1 Secure session handling
Tight session handling reduces harm from stolen access or compromised devices. Sessions should time out after inactivity and shut down when behavior looks off.
Session data belongs on the server. Tokens and secure cookies protect it. In some cases, limiting users to a single active session further reduces abuse.
Threats addressed:
- 1.1 Phishing and smishing;
- 1.2 The impact of AI on social-engineering attacks;
- 2.2 Device loss and theft;
- 3.1 Mobile malware and banking trojans.
Recommended #2 Patch management and dependency control
Robust security requires regular security updates. There are several great tools we use for that: OWASP Dependency-Check, Snyk, and GitHub’s Dependabot. They automatically scan the project’s dependencies for known vulnerabilities and suggest updates. Moreover, there are multiple handy websites that monitor the latest vulnerabilities and publish patches to them. The most reputable are:
- Common Vulnerabilities and Exposures (CVE).
- National Vulnerability Database (NVD).
- OWASP Top 10.
Threats addressed:
- 3.1 Mobile malware and banking trojans;
- 3.2 App-level weaknesses.
Recommended #3 Safe error handling and logging
Error messages can leak clues. Apps should show users only simple, neutral messages while keeping detailed logs on the server.
Central logging and monitoring help catch suspicious activity early and support investigations without giving attackers extra insight.
Threats addressed:
- 3.2 App-level weaknesses;
- 3.5 UI redress and clickjacking.
Recommended #4 Behavioral analytics and anomaly detection
Behavior tracking adds a flexible defense layer. It spots actions that fall outside normal user or device patterns.
This is especially useful against AI-powered social-engineering that slips past login checks. By linking session flow, transaction behavior, and device signals, banks can stop fraud before money moves.
Threats addressed:
- 1.1 Phishing and smishing;
- 1.2 The impact of AI on social-engineering attacks;
- 3.1 Mobile malware and banking trojans.
Addressing user-driven risks through design
Users make mistakes. Good design makes those mistakes harmless.
User behavior always affects mobile banking security. Relying on attention and caution does not scale. Modern apps reduce risk by shaping behavior through defaults and built-in safeguards.
The aim is simple: everyday actions should not turn into incidents.
Secure-by-default configuration
Mobile banking apps should start in a locked-down state. Strong authentication, short session lifetimes, and limited permissions should be on from day one.
When fewer security choices are left to users, fewer protections are weakened by accident.
In-app communication and user guidance
Clear in-app signals help users tell real actions from fake ones. Internal messages, transaction confirmations, and short warnings guide users at the exact moment decisions are made.
Well-timed alerts about unusual activity reduce the pull of phishing and smishing without relying on memory or prior training.
Monitoring and automated response
Ongoing activity checks help spot trouble early. When risk rises, the system can react on its own: ask for extra verification, slow a transaction, or pause access.
This shifts protection from user judgment to system response.
Device and environment awareness
Apps can read signals from the device and its surroundings. Device integrity, system version, and network traits all help estimate risk in real time.
When conditions look unsafe, the app can tighten controls or request extra checks to keep accounts protected.
How do I know all this? I implement these measures in SumatoSoft
SumatoSoft is a reliable outsourcing software development company that became a technical partner to many businesses. We build software for multiple industries: eCommerce software, Elearning development, Financial software development, healthcare software development, Real Estate, Logistics software, Banking IoT development, Travel, and more. We implement all measures from the article when dealing with mobile banking security.
Facts about SumatoSoft:
- We strive for quality and security and ISO 27001 and ISO 9001 certificates can prove it.
- We focus on long-term cooperation. 70% of our Clients come back to us with another project.
- Our Client’s satisfaction rate is 98%, thanks to our firm commitment to deadlines and their needs.
- Your project data stays safe. We guarantee the security of all data related to your project
- We only release the software if it meets the specified percentage of acceptance criteria. The percentage is agreed upon with you in the quality assurance strategy.
- 70% of our team is senior-level developers and QA engineers who ensure the app complies with domain best practices and our inner quality assurance guidelines.
When looking for a strategic IT-partner for the development of a corporate ERP solution, we chose SumatoSoft. The company proved itself a reliable provider of IT services.
We are pleased to mention that the work Is done to the full extent, on time and on a high quality level. It complies with the requirements due to the highly skilled project team of our chosen partner.
The work is fulfilled with due regard for the peculiarities of the project, namely:
- Domain complexity of the business solution;
- Raised standards for the implementation rate;
- Early consideration of the system’s scope and complexity when developing the solution’s architecture.
We recommend SumatoSoft as a reliable partner in the sphere of development and implementation of complex business solutions.
Get in touch with us for a free consultation. Let’s build a new product together!
Afterwards
So, mobile banking security is an achievable goal. It indeed requires the usage of multiple methods and techniques, but the final result is worth it.
The importance of technical security is out of the question, however, I want to highlight the users’ role: they must be actively engaged in protecting themselves. Even the most modern security methods, technologies, and techniques couldn’t protect a user with a rooted device who installs applications from dubious unofficial sources, doesn’t set a password for device lock, ignores two-step authentication methods, uses public wi-fi for transferring sensitive data, and isn’t aware of fraud schemes.
Robust mobile banking security is a collaborative effort of users and developers rather than a huge number of used security techniques.
Thank you for reading.
Let’s start
If you have any questions, email us info@sumatosoft.com