Guide to Enterprise IoT Security: Mitigating Risks in a Connected Ecosystem
This is a framework with steps and understandable metrics that will help your enterprise IoT security reduce risk and eliminate the complexity that hinders security. This guide is helpful for information security managers, IoT and OT security managers, architects building the overall system, and product owners responsible for connected devices.
How we recommend that you use this material:
- Review the data layers and flow map.
- Complete the basic security hygiene checklist.
- Select priority controls.
- Implement the roadmap and checklists.
Our goal is to provide achievable milestones to mitigate risk and avoid disrupting operations. Reliable IoT security reduces downtime and fines, simplifies audits, lowers insurance premiums, and speeds up the rollout of updates by making the process more predictable.
Architecture and Data Flows in Enterprise IoT
To manage risk in an IoT network, you need a map of it and a clear view of your IoT infrastructure. An IoT system is divided into four layers: devices, edge and network, cloud and data, and integration with IT and OT. This diagram will help you understand where to make decisions about trust and key management.
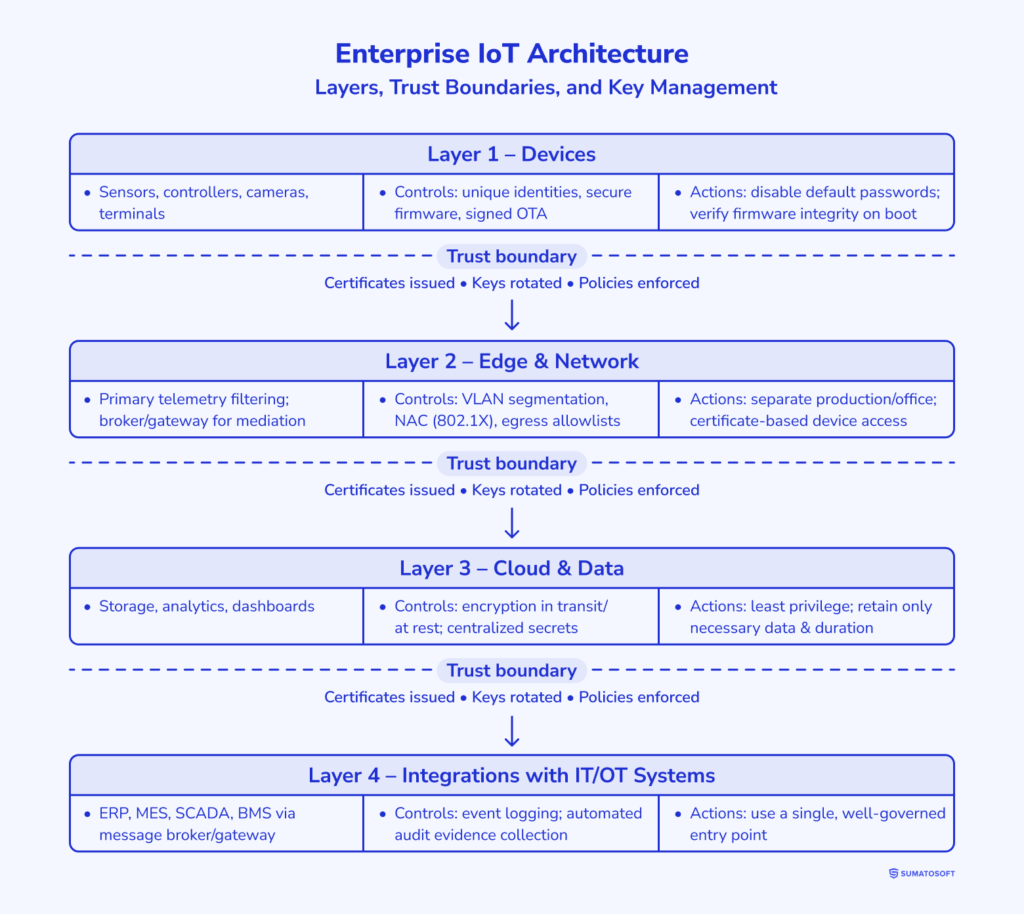
- Devices: sensors, controllers, cameras, and terminals. Unique identities, secure firmware, and signed updates are essential for these devices.
- What you need to do: disable default passwords and enable integrity checking at startup.
- Edge and network. This is where primary telemetry filtering occurs.
- What you need to do: segment traffic, separate production and office segments, restrict outgoing connections to whitelists, and use certificate-based device access control.
- Cloud and data. This is where storage, analytics, and dashboards reside.
- What you need to do: encrypt data in transit and in storage, manage secrets centrally, restrict service permissions, and store only the data you need and only for the required period.
- Integrations with information and operational technologies. A well-thought-out entry point reduces risk.
- What you need to do: connect external systems through a message broker or gateway, log events, and strive to collect audit evidence automatically.
Trust points are located at the boundaries between layers. This is where certificates are issued, keys are renewed, and policies are verified. Firm boundaries reduce the attack surface and downtime.
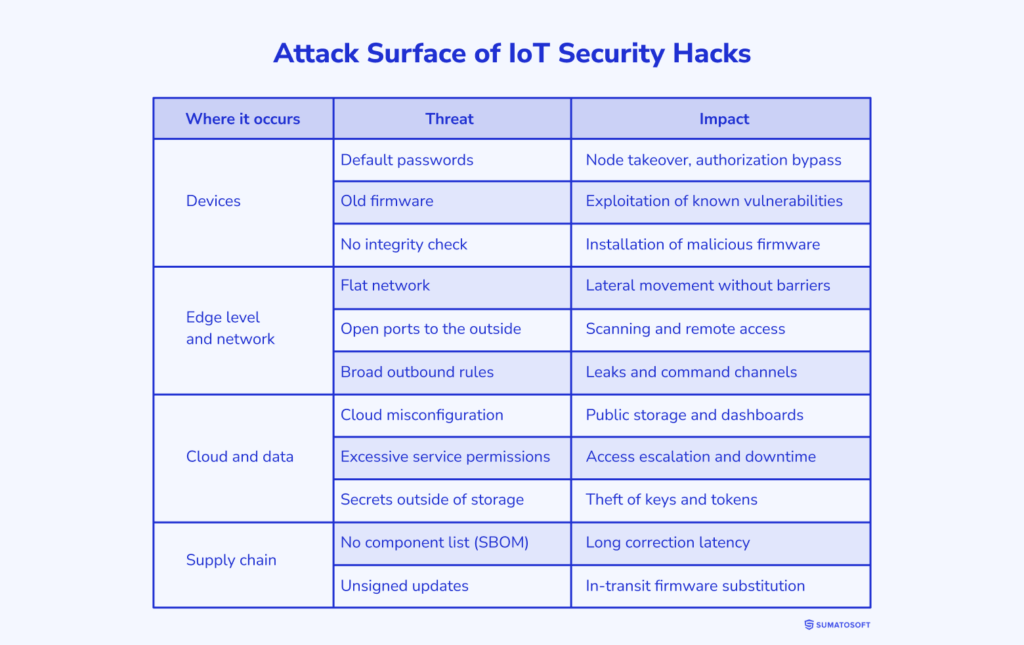
Attack Surface: How and Where Enterprise IoT Security Hacks Occur
The most common entry point for hackers is default passwords on devices or forgotten test access. The second route is a contractor with a laptop and unlimited privileges. The third is a cloud key stored outside the secret storage.
Once inside, the attacker looks for unprotected firmware or a service with administrator privileges. Without integrity checking, the device accepts a malicious image. Periodic network access provides them with a communication channel to the outside world.
A flat network helps them move further. Mixing production and office segments opens the way to dashboards and databases. Open ports on gateways expand the range of targets.
The first target is control panels and reports. Another is customer data and telemetry. Third, the actuators, where any failure equals downtime and costs.
If you suspect a breach in your network, here’s a list of red flags to watch for:
- slow firmware updates;
- percentage of devices without a unique certificate;
- increased outbound connections to unknown addresses;
- new devices not in the registry;
- service accounts with unnecessary privileges.
Here are the metrics you can track to catch attacks earlier:
- time to detect strange traffic;
- percentage of devices with updates in the last ninety days;
- number of blocked outbound connections per week;
- number of attempts to connect a new device without a certificate;
- isolation time for an offending node.
Basic Security Hygiene for the Internet of Things
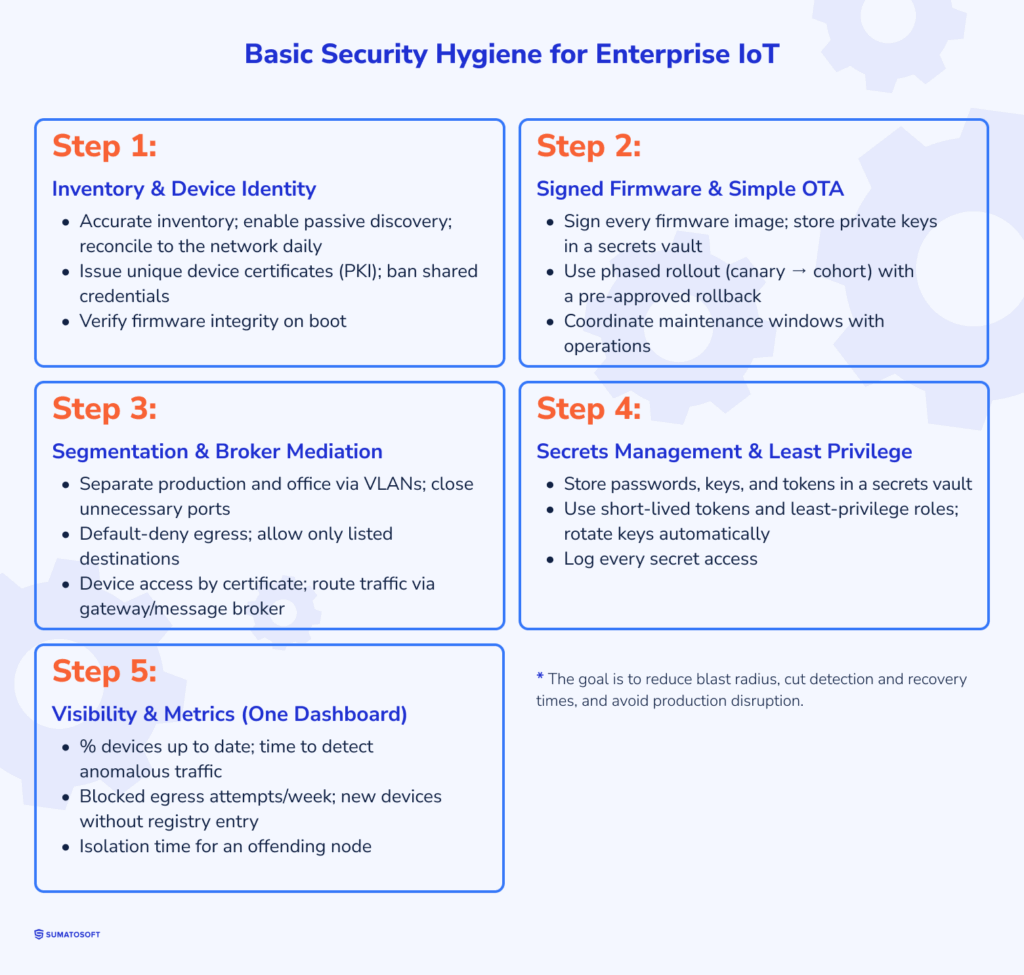
You can adhere to basic security hygiene practices and achieve results within the current quarter without interfering with production.
The first step is device inventory and identity. Here, you’ll ensure there are no shared credentials and that device startup verifies the integrity of the firmware image. When inventory and identity are in place, you see who is who. You can quickly revoke access if there is any suspicion.
- Collect an accurate inventory.
- Enable passive discovery.
- Check the network against the inventory daily.
- Issue each device a unique certificate via a public key infrastructure.
The second step is to sign each firmware image and adopt a simple IoT update management policy. Here, you ensure that private keys are stored in a secret vault and deployment is phased: starting with a small group, then proceeding to a larger one. This way, you close vulnerabilities without widespread failures and late-night crunches.
- Prepare a rollback to a verified version in advance.
- Coordinate update windows with operational teams.
The third step is segmentation. It reduces the damage radius, log noise, and response times.
- Employ virtual networks to separate production segments and office segments.
- Route all communication through a gateway or message broker.
- Close unnecessary ports.
- Block outgoing connections by default, allowing only the specified addresses.
- Allow devices to access the network only using certificates.
The fourth step is to control secrets and prohibit the sharing of credentials. The following measures will make the theft of a single secret almost useless.
- Conseal passwords, keys, and tokens live in a secret vault.
- Introduce short-lived tokens.
- Grant services only the required privileges.
- Set up automatic key changes.
- Log all access to secrets.
The fifth step is about visibility and metrics. You’ll need to oversee five metrics on a single dashboard to understand the current dynamics:
- the percentage of devices with current updates;
- time to detection of strange traffic;
- number of blocked outgoing connections per week;
- number of new devices without registry entries;
- isolation time for an offending node.
IoT Controls Best Practices
The asset discovery mentioned in step one of the previous section is just the first step in enterprise IoT security. Even large-scale programs don’t see everything. In an industry review, a company found over two million devices and still didn’t close the list. In addition to discovering nodes, a platform must understand vulnerabilities, assess risks, and apply protection.
What’s important to have beyond the inventory are complete device identification, flow and class mapping, and vulnerability management, including for legacy models without support. Segmentation and access rules should be modifiable based on threat signals, and network and device monitoring should enable rapid changes to access.
Device Identity and Public Key Infrastructure
- Purpose: To give each device a verifiable identity and managed trust.
- How it works: The device receives a certificate, and its key is stored in a secure module. Connections are made using certificates, and keys are changed on a schedule and when a risk arises.
- Where to use: All new devices and critical components. You’ll need to develop a transition plan for older models.
- Metrics: Percentage of devices with valid certificates, revocation time of a compromised certificate, and the number of access denials without a certificate.
- Mistakes: Sharing credentials, storing keys in file systems, and long rotation intervals.
- Case insight: Raise3D. We’ve reached out to companies operating IoT fleets, and a Raise3D representative has agreed to share the security measures they use to manage their fleet. Raise3D operates multi-printer FFF fleets in R&D and customer demo labs, with printers, edge gateways, and cloud monitoring. They’ve implemented 802.1X with device certificates and allow lists for the print server and the cloud, resulting in 70 percent fewer network scans on printer VLANs, zero unauthorized connections, and node isolation completed in five minutes.
Secure Boot and Signed Over-the-Air Updates
- Purpose: To allow only verified firmware and secure updates to run.
- How it works: Boot verifies the image signature, updates are signed, deployment occurs in waves, and rollbacks are prepared in advance.
- Applications: Cameras, gateways, controllers, panels, meaning any device that could stop the process.
- Metrics: Firmware vulnerability patching time, percentage of nodes running the latest version, and percentage of rollbacks after updates.
- Mistakes: There’s a signature, but the keys are unprotected. Update waves are too large, and there are no rollbacks.
- Case insights: In July 2025, Google partnered with Human Security and Trend Micro to uncover BadBox 2.0, the largest known botnet of internet-connected TVs. 10+ million smart TVs, digital projectors, in-car infotainment systems, and digital picture frames were compromised. The malware spread through pre-installed software on the device before purchase, retrieved from a command-and-control (C2) server contacted by the device on first boot, or downloaded from third-party app marketplaces. Infected devices were enrolled into a global botnet used for click-fraud campaigns, account hijacking, residential proxy services, and DDoS attacks. The operation relied on BadBox’s ability to evade threat detection by blending in with legitimate network traffic and leveraging the vast reach of consumer IoT to scale its activity worldwide. The cure was to enable signature verification at launch and a signed OTA. Affected companies implemented phased waves and instant rollback, preventing firmware-based reinfections and reducing update downtime.
Network Segmentation and Message Broker Mediation (Zero Trust Approach)
- Purpose: To cut down on lateral movement and narrow the blast radius.
- How it works: Production segments are separated from office segments. Devices communicate through a broker or gateway. Outgoing connections are allowed only through an allowlist.
- Applications: Workshops, warehouses, data rooms, and laboratories, especially in areas with multiple vendors.
- Metrics: Number of blocked outbound connections per week, node localization time, and percentage of traffic passing through the broker.
- Mistakes: Flat network for convenience, open ports just in case, and overall increased exceptions without revising the rules.
- Case insight: Dynamo LED Displays shared with us that they set up a “default block” for outgoing traffic on all controllers, leaving only the required directions, blocking 94% of connection attempts to unknown addresses. Incident resolution speed increased by approximately 30%, and implementation of these measures took less than a week.
Secret Management and Minimum Privileges for Services
- Purpose: To protect passwords, keys, and tokens. To eliminate unnecessary privileges for services.
- How it works: Secrets are stored in a secret vault, tokens are short-lived, access is granted based on roles, and rotation is automatic.
- Where to use: Panels, vaults, message brokers, cloud functions.
- Metrics: Average age of secrets, share of services with short-lived tokens, and failures due to insufficient privileges.
- Mistakes: Keys in code or in the repository, shared credentials, and ultra-broad roles.
- Case insights: Mars Hydro, a grow-light manufacturer, had 2.7 billion records leaked due to a cloud configuration error and weak key management. The leak was fixed by using secret storage, eliminating unnecessary privileges, introducing private networks, and blocking outbound connections not on a list. Thus, the company closed the open database, reducing the risk of re-indexing and leaks.
Vendor Risk, Software Component List, and Patch Agreements
- Purpose: To manage supply chain vulnerabilities.
- How it works: Vendors must provide a software component list and vulnerability notifications. Patch agreements are implemented. Workaround plans are established in advance.
- Where to use: Procurement, acceptance, upgrades, and equipment monitoring in buildings, workshops, and transport.
- Metrics: Average time to patch vulnerabilities by vendor, percentage of vendors with a complete list of software components, and percentage of devices running supported versions.
- Mistakes: Lack of a component list and disclosure policy, and installation of outdated models with no support period.
- Case insights: Robots in industry, as in the case described by AEM × TÜV Rheinland in 2025. Networked robots ran on old systems with weak passwords and open ports. Flat networks and vendor-remote boxes widened access to controllers and safety interlocks, allowing attackers to change logic, stop lines, or steal code and process data. The solution was to use IEC 62443-3-3 as the base and set security levels, which involved splitting cells into zones and conduits, encrypting robot and controller traffic, replacing default passwords with device identity, and enforcing rotation and lockouts. The result was a smaller blast radius, faster detection and response, and fewer unsafe changes. Robot production plants saw fewer unplanned stops, cleaner audits, and a drop in exposed services, while vendors got clear targets for fixes, and upgrades followed a safer, staged process.
Border Layer Hardening and Data Minimization
- Purpose: To stop unnecessary traffic at the network edge and prevent unnecessary traffic from reaching the cloud.
- How it works: Gateway policies filter traffic, personal data is stripped on the spot, data is compressed and aggregated, and storage receives only the necessary fields for the required period.
- Applications: Industrial gateways, controllers, and telemetry collection points.
- Metrics: Data volume going to the cloud, percentage of records without unnecessary fields, and number of blocked outgoing connections.
- Mistakes: Collecting all data, opening outgoing connections to the entire internet, and failing to check the field composition.
- Case insights: Nortek, a company that produces oceanographic and subsea navigation solutions, began experiencing issues with weak passwords and access controller vulnerabilities. To fix that, the company isolated devices, closed unnecessary ports, and reduced data to the bare minimum, reducing the number of entry points. The result was a faster response to suspicious events.
Field Team Access and Work Instructions
- Purpose: To grant teams access when needed without disrupting the process.
- How it works: Pre-arranged unscheduled access, quick rollback preparation, and step-by-step updates. Instructions should be brief, verified, and available offline.
- Applications: Field teams, remote sites, sites with limited windows.
- Metrics: Response and recovery time, successful rollback rate, and number of bricked devices.
- Mistakes: Lack of instructions and rollbacks, leading to escalations that take hours to resolve.
What’s in It for Enterprises Employing IoT?
Segmentation and allowlisting reduce unnecessary connections and noise; secure boot and signed updates reduce the attack window. Device identity and secret management simplify access and provide audit evidence, while continuous inventory allows you to prioritize repairs. All these measures work without costly fleet replacements.
Assessing Business Impact and ROI
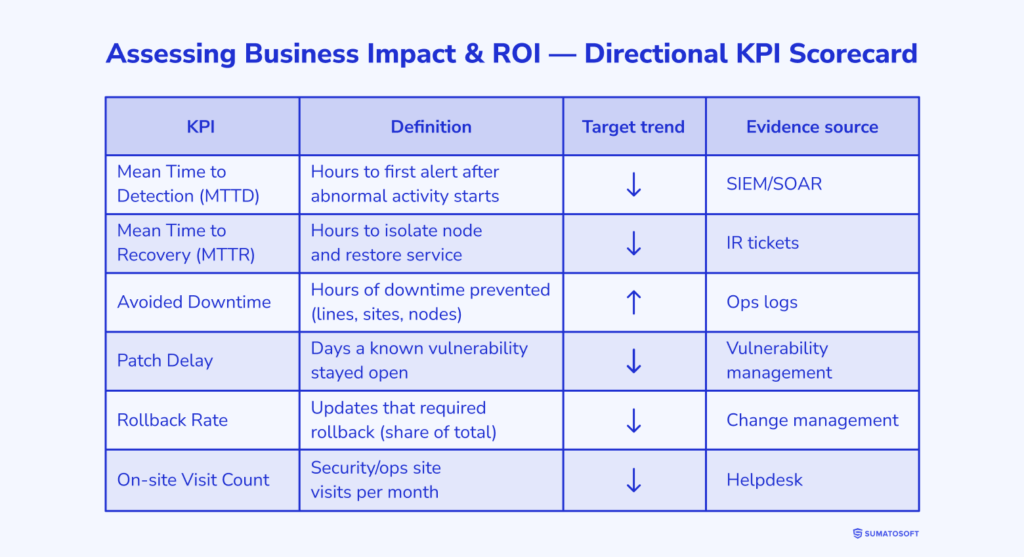
We measure the impact of introducing enterprise IoT security measures using six metrics from our IoT ROI framework.
- Mean time to detection, i.e., how many hours did it take the system to respond to the first alert. Fewer hours mean less downtime.
- Mean time to recovery, i.e., how many hours did it take to isolate a node and restore service. Fewer hours mean fewer losses.
- Avoided downtime, i.e., how many hours of downtime you avoided. We calculate this by lines, warehouses, and nodes.
- Patch delay, i.e., the number of days the vulnerability remained open. Fewer days mean a smaller attack window.
- Rollback rate, i.e., the number of updates that had to be rolled back. Fewer rollbacks mean a more stable release.
- On-site visit cost, i.e., the number of visits avoided.
Then we connect these metrics with costs.
- Cost per hour of downtime multiplied by the hours of downtime avoided = savings.
- Cost per team hour multiplied by the reduced recovery hours = savings.
- Reduction in the number of response trips multiplied by the cost per response = savings.
- Payback = (savings – implementation costs) divided by the implementation costs.
- Payback period = costs divided by the monthly savings.
To calculate before-and-after, take three months before and three months after the implementation of the measures, and compare the metrics. Check how the following have changed: time to detection, time to recovery, number of response trips, rollback frequency, and days to patch deployment. Associate each metric with a monetary value using the formulas above.
Conclusion
Enterprise IoT security is a system: a layer map, strict trust boundaries, managed controls, and metrics. Once the system is assembled correctly, risk is reduced. Complexity should no longer hinder update releases and site operations.
Treat asset discovery as the start, followed by classification, vulnerability assessment, segmentation, signed updates, and secret management. You’ll see the impact in the budget: less downtime, fewer site visits, faster recovery, and cleaner audits.
Consider average time to detection and recovery, hours of avoided downtime, patch deployment delays, rollback rate, and site visit costs, and link each metric to a budget and see the trend.
Make sure your IoT devices have certificates and secure boot, and that OTA updates are signed and include rollback protection. Your custom IoT software development should have protocol coverage, a component list, vulnerability applicability notifications, integrations with security event management systems and IT service management systems, and finally, a transparent update policy and support timelines.
The rest is a matter of conducting a short self-assessment across four layers and establishing basic hygiene: device inventory and identity, segmentation and allowlists, signed updates, and secret storage.
How SumatoSoft Can Help
SumatoSoft bridges the gap between enterprise security and the Internet of Things through IoT security and compliance services. We work with industrial plants, warehouses, healthcare networks, and smart buildings. We’ll conduct a quick assessment of your IoT fleet in two weeks, covering inventory, flows, risks, and fast actions, and will offer most plausible for your case IoT fleet management solutions. Then, we’ll be able to design and implement device certificates, secure boot, and OTA policy with rollback. We’ll deploy networks and configure a broker with a single point of entry, allowlists, and outbound connection control. Your secrets will be in order with a storage, short-lived tokens, and key rotation. We’ll connect metrics to finances, so you’ll understand your long-term business benefits of getting IoT security measures straight.
Want to reduce risk without closing your lines? Contact SumatoSoft for a consultation and implementation on IoT security. We’ll start with a short session, set quarterly goals, and consolidate metrics so that you can see less noise, less downtime, and clear returns in just a quarter.
Let’s start
If you have any questions, email us info@sumatosoft.com