Main Principles: Application Security Testing


Nowadays, security is a major topic in the IT industry. News like Apple’s iOS encryption dispute with the FBI or attack on NASA’s website were among the biggest headlines. Major data breaches, bank heists, account hijacking, hacktivism and DDoS attacks – the crime list is huge. No wonder the panic is only growing as cyber-criminals are becoming more and more tech-savvy and organized. So it’s fair to say that the problem of software security testing is actual as never before.
This is why we invited SumatoSoft QA engineer Dmitri Reginevich to share his thoughts and knowledge on security testing. This article represents a summary of Dmitri’s report from “Technical Breakfast” – a regular office-based event which helps our employees, both from the development and marketing departments, obtain more expertise in various IT-oriented topics.
As a term, security testing is a policy used to test the security level of a system, as well as the analysis of the risks associated with providing a holistic approach to application security, hacker attacks, viruses, and unauthorized access to sensitive data SPF flattening is a must for security if you have mailing involved..
The software’s security is marked by:
- the ability to counteract to unauthorized interference with the software;
- the ability to prevent the attempts of stealing and using the data;
- the ability to counteract attempts to destroy the software and the data it uses;
The subjects to protection are:
- data;
- reliability and performance;
- functions of the software product;
Which Is The Most Secure Country in the World
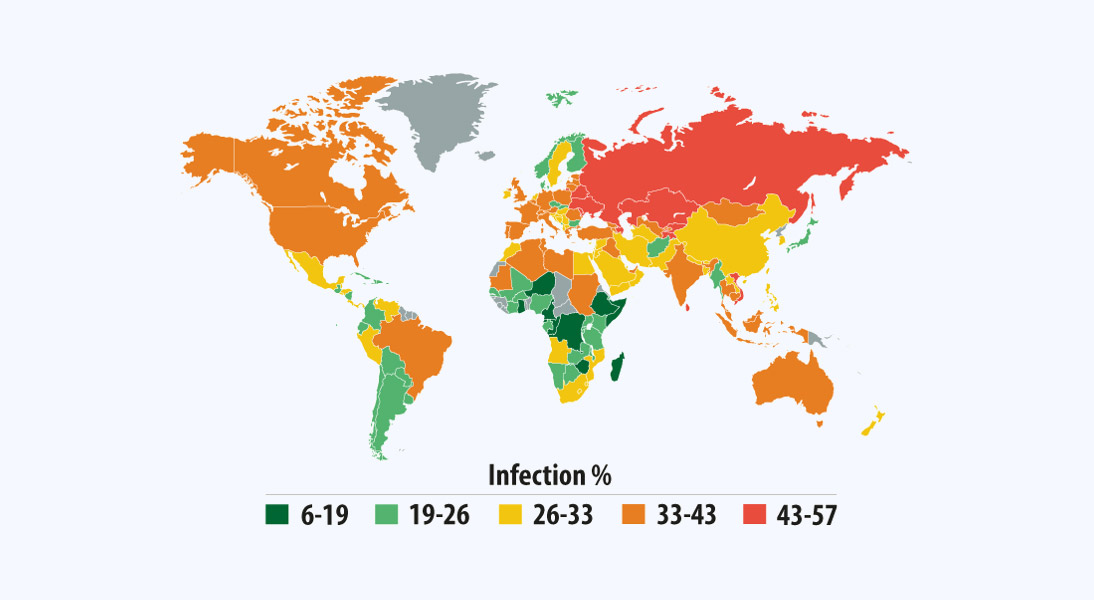
The 2023 cybersecurity risk report presents a sobering reality: there is no such thing as a completely cyber-secure country. Analyzing 75 nations across an extended list of 15 criteria, the study paints a picture of a complex and uneven global cybersecurity landscape. Even Denmark, which emerged as the most cyber-secure nation, had its vulnerabilities, emphasizing that cyber threats are an ever-changing and universal concern.
The impact of COVID-19 further complicated this landscape. The pandemic led to a significant rise in cyber risks, with malicious activities such as disguised files for virtual meeting tools surging by over 1000 percent. Countries that seemed to have robust cybersecurity measures were not spared either, indicating that existing defenses are insufficient against evolving threats.
The study serves as a wakeup call, emphasizing that cyber threats are pervasive and no country can consider itself completely secure. This underscores the pressing need for a comprehensive, continually updated approach to cybersecurity at both national and organizational levels. As cyber threats grow in complexity and reach, it’s evident that complacency is not an option, and continuous vigilance is the need of the hour.
Hacker Classes

Hackers can generally be classified into different types based on their motives, methods, and whether they operate within the boundaries of the law. Here’s a brief overview:
- White Hat Hackers: These are ethical hackers who use their skills for good, often to test systems for vulnerabilities so that they can be fixed. They usually work with the permission of the organization that owns the system.
- Black Hat Hackers: These hackers engage in illegal activities for personal or financial gain, or sometimes just to cause chaos. They exploit vulnerabilities in systems without permission.
- Grey Hat Hackers: Falling in between White and Black Hat hackers, Grey Hat hackers may break the law but often do so with good intentions—such as exposing a vulnerability to the public if an organization fails to fix it.
- Hacktivists: These are hackers who use their skills to promote or support a social, political, or environmental cause. Examples include groups like Anonymous.
- Script Kiddies: These are unskilled individuals who use pre-written software or scripts to perform hacks, but don’t usually understand the underlying technology.
- Red Team Hackers: These are professionals employed to mimic potential attackers on a system. Their goal is to discover vulnerabilities from an attacker’s viewpoint to better secure systems.
- Blue Team Hackers: Opposite to Red Team hackers, the Blue Team aims to defend an organization’s information system and is responsible for patching up the vulnerabilities discovered by the Red Team.
- Cybercriminals: These are individuals or groups who commit fraud, theft, or other crimes using computer technology. While similar to Black Hat hackers, the term emphasizes criminal profit as the primary motive.
- State-sponsored Hackers: These are hackers employed by governments to collect intelligence or disrupt enemy capabilities.
- Green Hat Hackers: These are beginners in the hacking world, keen to learn. Unlike Script Kiddies, they aim to gain deeper understanding and usually evolve into one of the other types of hackers.
- Purple Team Hackers: These are individuals or teams that aim to combine both offensive (Red Team) and defensive (Blue Team) strategies to improve security.
- Neophyte: These are individuals who are new to hacking and are in the process of learning the ropes. They may not yet have decided what type of hacker they want to be.
These classifications can help you understand the various roles that hackers can play in the world of cybersecurity.
6 Security Principles
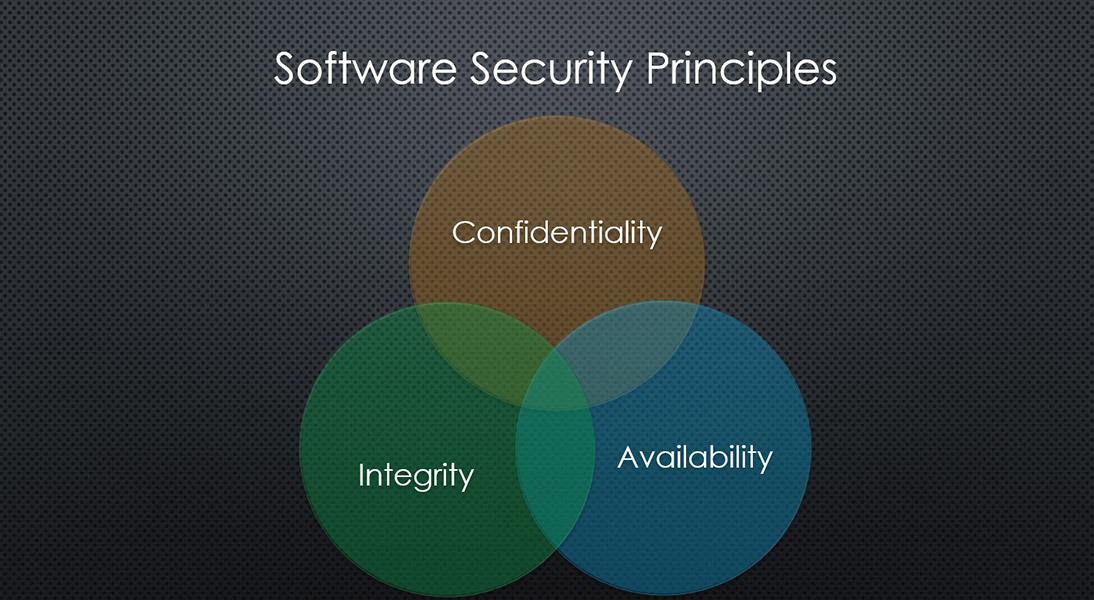
Core CIA Principles
- Confidentiality ensures that sensitive information is only accessible by those with the proper permissions. This is critical in settings such as healthcare, where medical records should be confidential, or in business, where proprietary information should be kept secret. Encryption and access controls are commonly used methods to maintain confidentiality.
- Integrity – this principle ensures that the data remains unchanged during storage, transfer, and retrieval unless altered by an authorized entity. Hash functions and checksums are often used to verify integrity. Data integrity is essential for things like financial transactions, where even a small change in data could have significant ramifications.
- Availability – this ensures that information and resources are available when needed. This is crucial for emergency services, online banking, e-commerce, etc., where downtime could result in life-threatening or financially damaging consequences. Methods to ensure availability often include redundancy, failover systems, and Distributed Denial of Service (DDoS) protection.
Complimentary Three Principles
- Authentication – while confidentiality ensures that only authorized people can view data, authentication ensures that those people are who they claim to be. It’s the process of confirming the identity of a person or system. Various methods like passwords, multi-factor authentication (MFA), and biometrics are used for authentication.
- Authorization – after a user has been authenticated, the system must then determine what actions they are permitted to carry out. This is the role of authorization. Role-based access control (RBAC) and discretionary access control (DAC) are commonly used models for authorization.
- Non-Repudiation – this is vital in legal and financial transactions where the parties involved must not be able to deny the authenticity of their participation. Digital signatures and timestamps are usually used to ensure non-repudiation.
The CIA Triad often serves as a comprehensive framework for understanding the various aspects of cybersecurity. The additional principles of Authentication, Authorization, and Non-Repudiation augment this framework, providing a more complete picture of what’s involved in establishing a robust cybersecurity posture.
Being security testing adepts, we follow these principles in full measure. If you have any questions about your application security, feel free to get in touch with our team. We’ll be glad to help you!
Let’s start
If you have any questions, email us info@sumatosoft.com